2017-09-22 10:17:00 -0400
As noted earlier this year on our discussion forum, we’ll be discontinuing the iPad-only version of Codebook that’s currently available in the iTunes App Store. We’d like all our customers who purchased that version of the app to install the other, universal (i.e. runs on iPhone and iPad) version of Codebook now that it runs on both device types.
Previously, both apps used the same blue icon and had the same name on the Home screen, “Codebook”, making it hard to tell the apps apart. To aid in the transition and help give our iPad customers a heads-up that things are a-changing, we gave Codebook for iPad’s app icon an update, switching it to black and white.
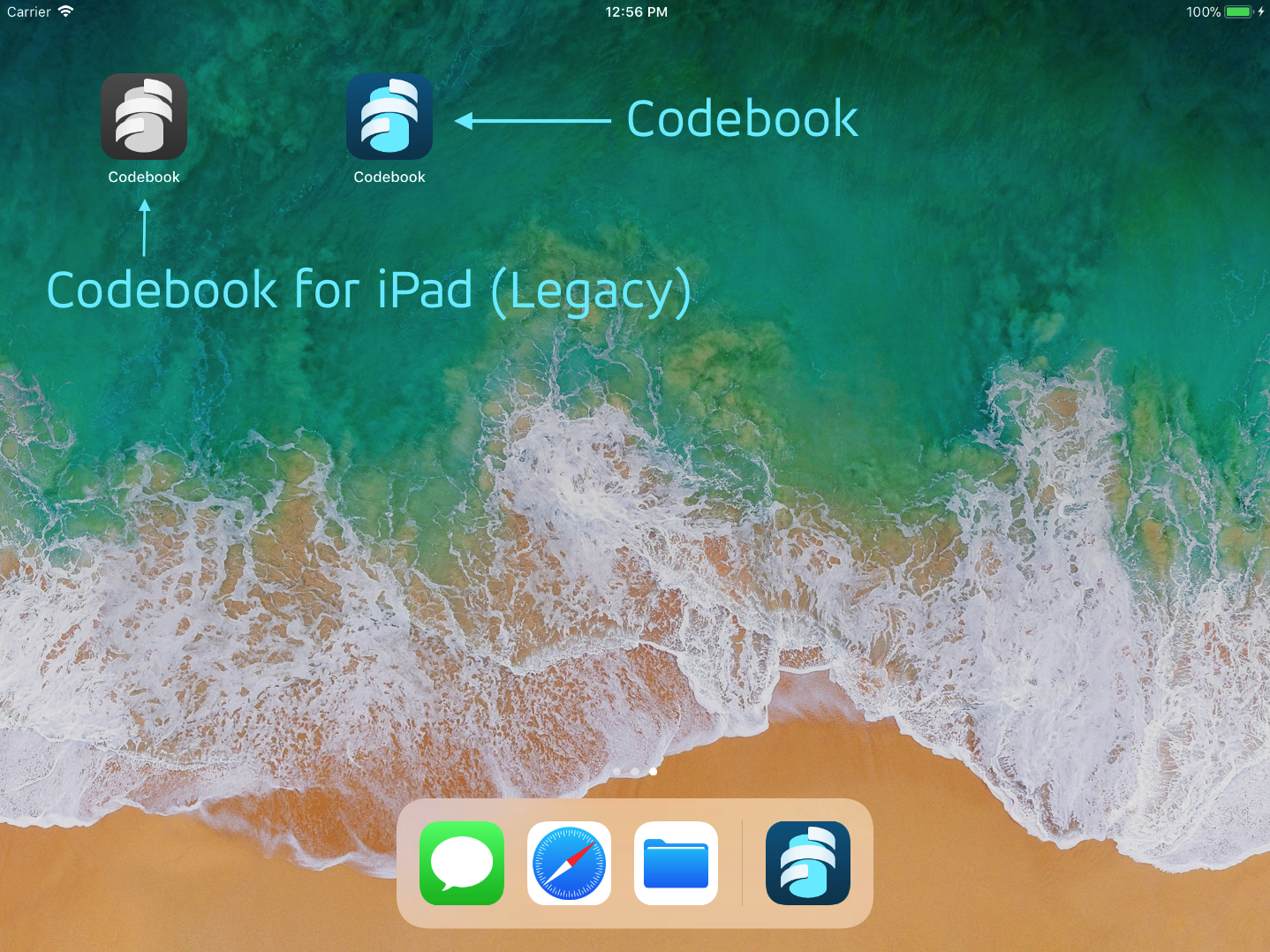
Transitioning to the Universal Codebook
First, you’ll want to install the newest version of the universal Codebook for iOS app on your iPad alongside the old version with the black and white icon (don’t delete anything just yet!) Visit this link directly on your iPad to be taken to the right page in the App Store. If you don’t already own the iPhone version, not to worry: we created a bundle in the App Store allowing you to credit your iPad purchase towards the iPhone version, which should result in no charge for most customers.
Once installed, launch the app and go through the first-time setup process, using the same password you usually use to protect your Codebook data.
During setup you will be given an opportunity to use Codebook’s Sync feature to copy your data over from another install of Codebook on the desktop via WiFi, or via Google Drive or Dropbox. You’ll want to set the switch on this screen to Yes for a restore.
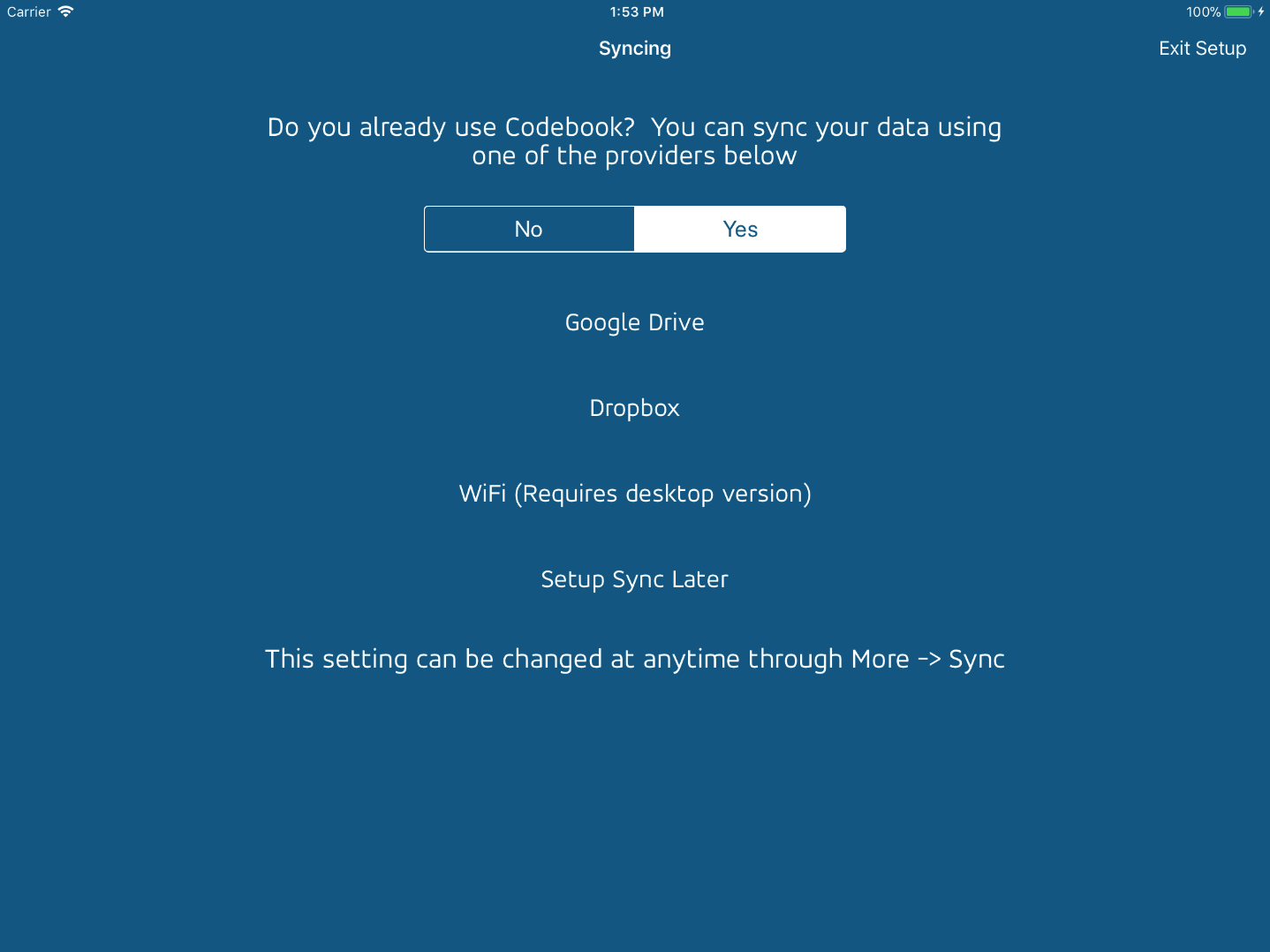
Once you’ve loaded your data into the universal build of Codebook (the one with the blue icon) you can safely remove the version with the black and white icon. Currently Codebook for iPad is still being maintained, but everyone using it should switch over to the universal version as soon as they can, as we will eventually remove it from the App Store.
2017-09-22 10:17:00 -0400
Properly configured projects using SQLCipher shouldn’t experience problems using Xcode 9. However, changes in the new SDKs can cause compile time errors for misconfigured projects, e.g.
Implicit declaration of function ‘sqlite3_key’ is invalid in C99
Implicit declaration of function ‘sqlite3_rekey’ is invalid in C99
We have prepared important recommendations for SQLCipher developers on how to resolve these problems on the SQLCipher support forums:
Important Advisory: SQLCipher with Xcode 9 and new SDKs
2016-09-14 13:20:00 -0400
Apple has released XCode 8 and new SDKs. We have published important guidance
for using SQLCipher with the new platforms (e.g. for iOS, watchOS, macOS, tvOS, etc.) on the SQLCipher support forums:
Important Advisory: SQLCipher with XCode 8, iOS 10, etc
Critical recommendations include:
- Adjusting Project Build Settings to link SQLCipher first
- Including an Application Runtime Check for SQLCipher
- Testing and Validation
Please make it a priority to implement these recommendations and perform appropriate application testing when moving to these new platforms.
2016-07-25 07:00:00 -0400
We’re happy to announce the release of Codebook for Mac 3.0.11 and Codebook for iOS 3.1.3 which introduce a new setup assistant to guide you through setting up Codebook for the first time, or on a new device.
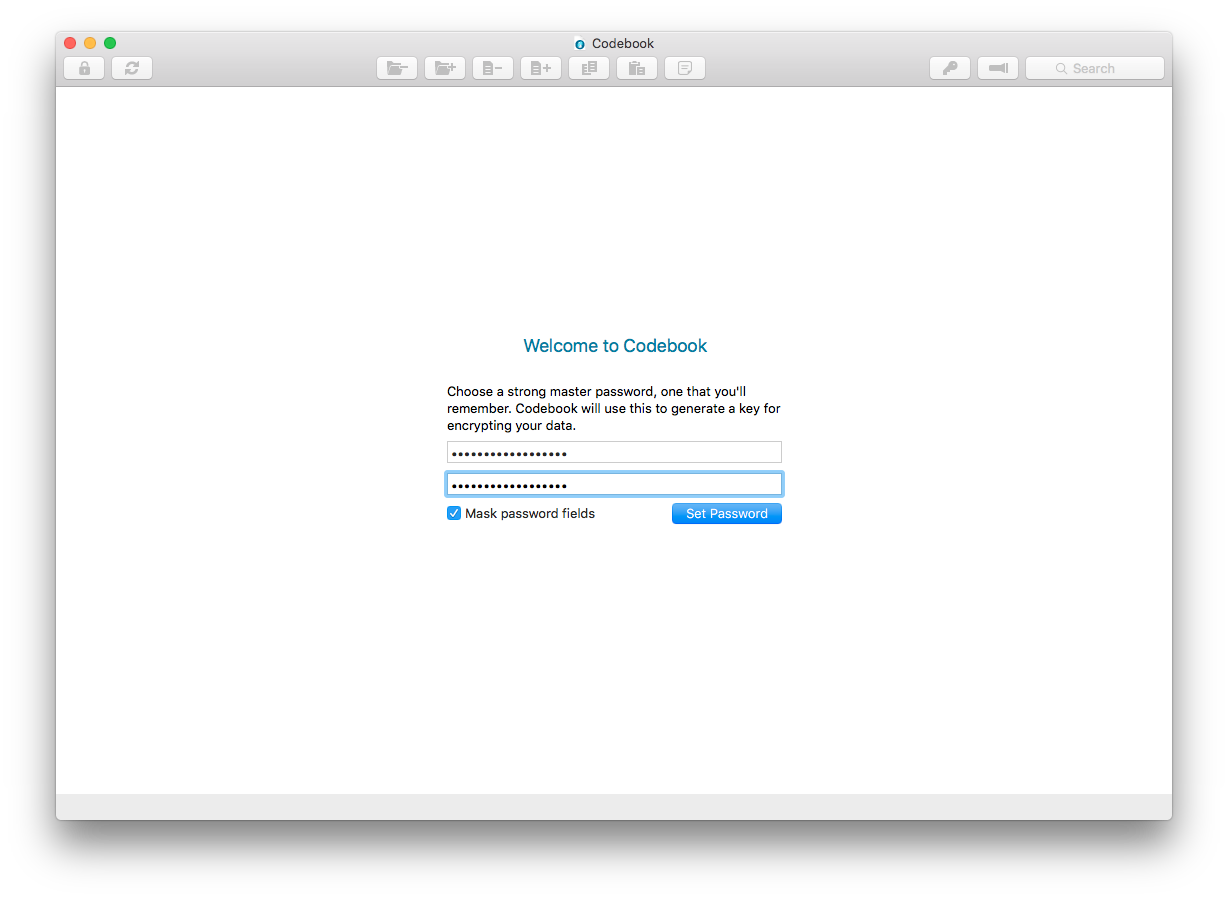
The assistant guides you through:
- Setting up your master password
- Enabling Touch ID on iOS (if available)
- Enabling Anonymous Statistics
- Setting up Sync or, if this isn’t your first time using Codebook, restoring your data.
The new first time setup experience may sound like it doesn’t apply to you, a long time and valued customer, but sometimes we need to install Codebook fresh or on a new device. The new first time setup experience provides the option of restoring your data during setup.
Editing From Secret Agent:
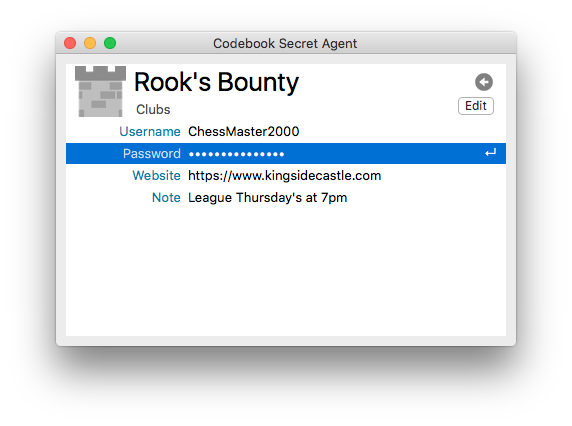
Sometimes we find ourselves needing to create or change a password and we automatically trigger the Secret Agent keyboard shortcut only to realize as soon as it comes up that it currently can’t help us with this. The Edit button on the entry view displays the Main Window, looks up the entry, and puts the interface in edit mode.
2016-07-18 06:00:00 -0400
Hey everyone, we have some very exciting news to share with all iOS and Android users in France: We are once again selling our well known password manager and note taker Codebook in the French iTunes App Store and the French Google Play Store!

It has been about 4 years since we had to stop selling Codebook (named STRIP at that time, Strip on your iPhone’s home screen) due to French laws regarding the selling of encryption software but we recently received approval to start selling our software in France again and we are really excited.
Upgrading from Version 1 to Version 3
Our existing customers in France stopped receiving iOS updates around version 1.6, and the current version is 3.1. We have tested the upgrade from the old STRIP versions to the new Codebook versions and there do not appear to be any issues. However, we recommend that you first backup your device to iTunes or iCloud or use the Sync feature to sync your data with a Dropbox account.
Name and Icon Changed - Codebook is STRIP!
STRIP was renamed to Codebook and it has a new icon on your iOS home screen:

If you currently get automatic updates from Apple, once the app is released in France, it will automatically update the current STRIP app to Codebook and replace the icon on your home screen. If you leave this setting on and notice that your STRIP icon is gone and you now see a new Codebook icon, this is OK, DO NOT delete it as this is the new version of STRIP. You can login with the same password you have been using for STRIP and all your data should be intact.
While We Were Away
There have been quite a few other changes to Codebook for iOS since version 1.6. A modern interface, fixes and improvements, and lots of new features. We’ve also created ports of Codebook for Android, macOS, and Windows, making your passwords available on other devices you use.
An incomplete listing of new features and improvements:
Need Help?
Please contact us at support@zetetic.net if you have any questions. You can visit our original announcement of the change from STRIP to Codebook to learn more about the transition.
![]()




