2016-03-29 06:20:00 -0400
We’ve been putting a lot of elbow grease into our password manager Codebook since the 3.0 update at the beginning of the year and we got to share some of that work in recent updates this month for iOS and Mac. On Monday March 14th we released 3.0.3 for Mac and Tuesday the 15th we released 3.0.4 for iPhone and iPad. Many of our point releases focus on a small number of issues, but this is a pretty big update between the two with dozens of bug fixes, improvements, a new feature, and improved security for Touch ID login on iOS. This is a free update for all customers.
The new Journal view
Journal is a new view in Codebook for iOS and OS X that shows all the notes in your database in one place, sorted either by the date the note was created or the date it was updated (up to you.) Notes are still stored in categories alongside multi-field records, this view makes it possible to keep track of those notes over time.
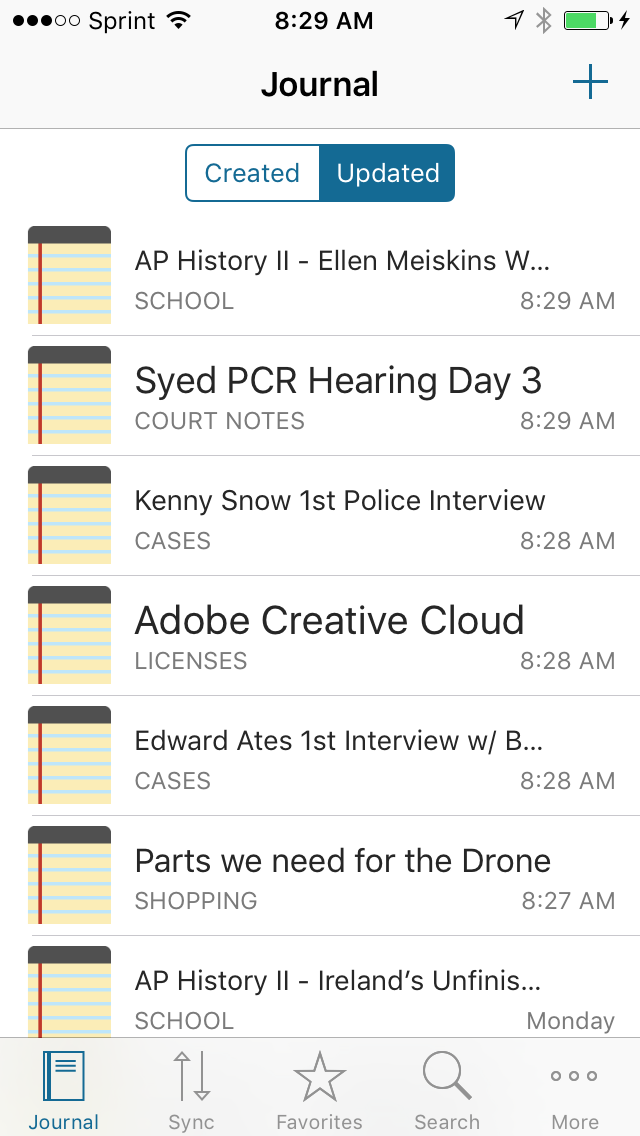
Were you a user of Codebook 2 on iOS? You can rearrange your tabs in Codebook 3 on iOS to show the Journal view first if you prefer to use the app as a secure notebook. Just tap on the More tab, then Edit, and arrange your tabs as you like:
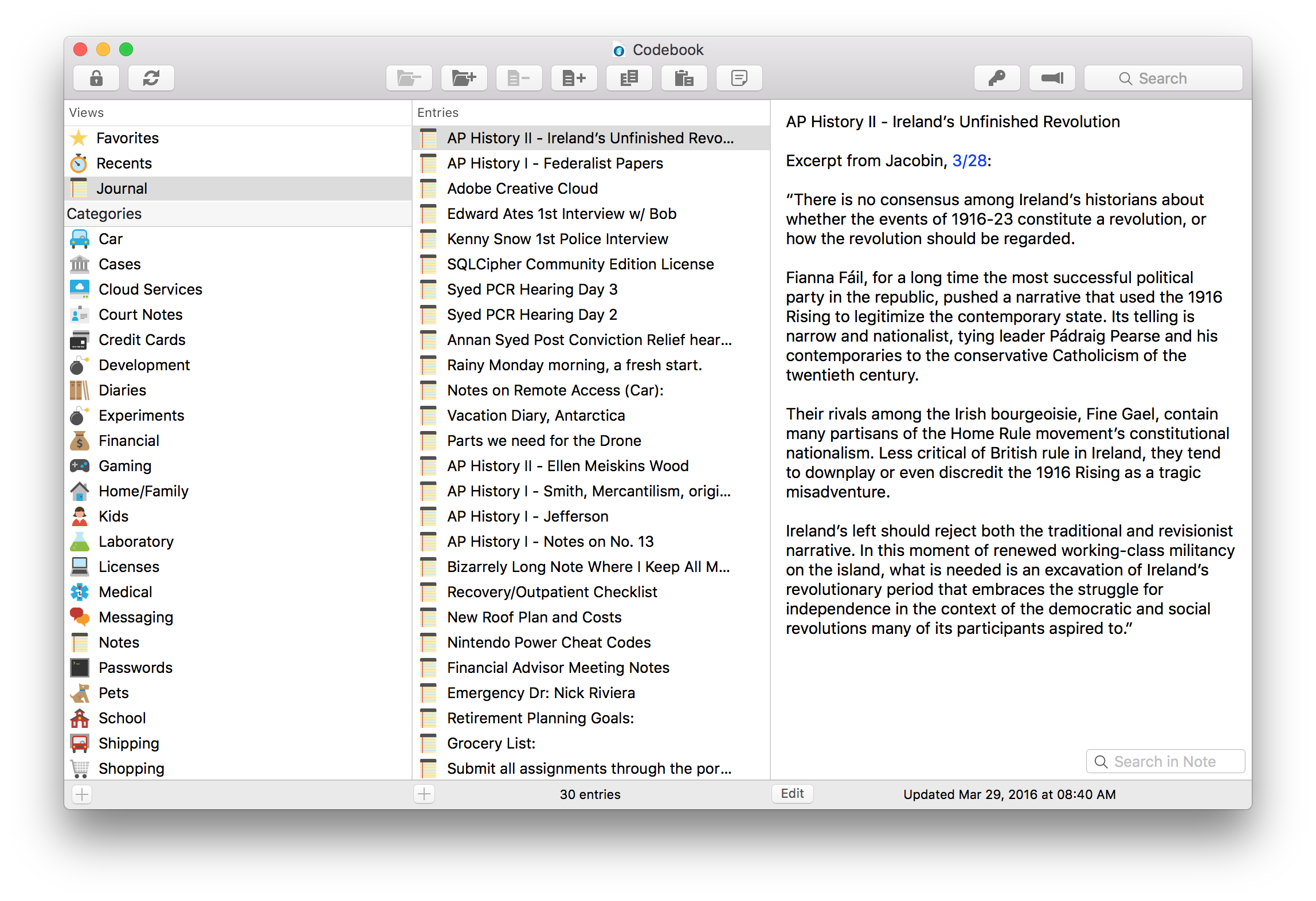
On OS X you can find Journal in the Views list (or access it directly by using the shortcut shift command 3), and the sorting preference is available under Preferences:
The Journal view will be coming to Windows and Android soon.
Improved Security for Touch ID Login
Codebook on iPhone and iPad offers a setting that allows the user to enable the use of Touch ID fingerprint authentication for logging in to Codebook. This makes it much easier to use a strong master password on mobile devices where typing it in can be a bit arduous.
Recently an attack on this was suggested by Per Thorsheim of Godpraksis and the Passwords conference, where another person with knowledge of your iOS device passcode (perhaps a family member) could use that to add their own fingerprint to the list of authorized fingerprints and thereby impersonate the owner at Touch ID prompts like the one in Codebook.
Fortunately, in iOS 9 Apple introduced some new security restrictions that we as developers can take advantage of to help prevent this. Version 3.0.4 improves Touch ID login for Codebook on iOS 9 in two ways:
- If Touch ID authentication is used with Codebook it will no longer allow fallback to the device passcode
- If changes are made to registered fingerprints in iOS Codebook will not allow Touch ID for authentication and require you to reenable this feature
To take advantage of these improvements sign in to Codebook, tap on the Settings tab, then Login Settings. There disable and then enable the Touch ID login feature.
Import and Export on Mac
Codebook for OS X has not always done a particularly stellar job when it came to importing data, especially large amounts of it. This version introduces a completely revamped Import feature that rips through large CSV files and is more tolerant of text files that aren’t encoded in UTF8.
Import on the Mac side no longer provides the ability to do bulk updates of existing records by including a column named EntryID. We never provided it on Windows and we’ve always been a bit skeptical of its utility. Now all rows are treated as new records to be created.
To facilitate the creation of Notes one can now include a column named Note Entry, each row with a value in this column’s field will be treated as Note rather than a multi-field Entry.
Export to CSV no longer includes the EntryID column, and provides the contents of Notes in the Note Entry field. There is also a new option on the Export dialog where you can select Plain Text output instead. This produces an unencrypted text document suitable for printing should you wish to have a hard backup of your data for safe storage.
Accessibility and Keyboard Shortcuts
Throughout Codebook for OS X we’ve been working to ensure that the application is fully accessible; any task one could accomplish with a mouse should also be available using the keyboard. We’re not all the way there yet but we’re on our way, adding new shortcuts where they were missing and improving the options available in the File and View menus. For instance, one can now access the new Views above the Categories list by using the shortcuts for them under the View menu (e.g. Use command 3 to select the Journal view). You can keep up with all our keyboard shortcuts here. We’ve also been going through the interface adding better labels for voice-over support for identifying controls. Coming soon: a Cut feature for entries, a keyboard shortcut for removing fields, and Undo for editing an entry (in case you really didn’t want to delete that field).
Stay tuned for more updates, we’ve got more good things coming for Codebook, big and small!
2016-02-22 06:00:00 -0500
Now that the dust is starting to settle with Codebook 3 it’s time to wind down Codebook 2. Currently the app is in maintenance mode; we have a minor bug fix update on the way, but no feature improvements planned. On July 4th, 2016 we will remove it from sale in the iTunes App Store. At that point it will no longer be available to download from the App Store, and may not be available for restore from an iCloud backup either. You will still be free to use the Codebook 2 software you purchased after that date, however, you must make regular backups in iTunes so that you have a copy of the app, or you will be at risk of losing access in the event of a device transfer or reset. It is also a good idea to ensure your Codebook 2 data is frequently backed up to Dropbox as well.
Backing up your Device (click Use iTunes)
If you are a Codebook 2 customer and are having trouble migrating your data (or deciding to upgrade), please get in touch with us at support@zetetic.net.
2015-12-14 07:00:00 -0500
We are very excited to announce some new and very important changes to the STRIP Password Manager:
- STRIP has been renamed to Codebook: The STRIP icon will be replaced with a new Codebook icon. All the logos, icons and colors are updated.
- Dedicated Notes: You can now store dedicated Notes in Codebook. These are perfect for storing longer, free-form text.
- Favorites: You can now mark your most important entries with a Favorite Star to make them show up in a dedicated quick access view and as the first entries returned in searches.
STRIP to Codebook 3 (and a bit of history)
One of the most visible changes is that STRIP is being renamed to Codebook, version 3. The application now has a brand new logo, icon, and color scheme to match, professionally designed by the excellent team from the Icon Factory.
Some of our most dedicated users will remember that STRIP was first released over 17 years ago for Palm OS. The acronym, Secure Tool for Recalling Important Passwords, seemed playful and unique at the time. However, the name hasn not aged as well as the application itself. Over time:
- Searches for the product started returning unrelated adult content
- People found the name potentially offensive
- The name became generally unwelcome among our customers
Thus, even though the application has became well known as STRIP, the time has come to change.
So, if you don’t see STRIP after you upgrade, don’t panic! The old STRIP icon will be replaced with a shiny new Codebook icon like this.

Some users may be aware that Zetetic previously released a different product named Codebook, a simple note taking tool for iOS, several years ago. After this release users of the old Codebook will have the option to migrate their data into the new Codebook application (more on that here - Migration Document).
Going forward, there will be only one Codebook!
Dedicated Notes
This brings us to one of the new features in this release: dedicated note entries. While standard entries are great for organizing the multitude of small fields and values that apply for most accounts, they are not optimized for larger bodies of free-form text.
A new “Notes” feature allows you to quickly and easily create text-based notes with a single tap, which can be organized separately or alongside other entries.
Favorites
Another major feature in the release is the ability to mark important entries as “Favorites”. By marking an entry with a Favorite star, the record will automatically show up in a new Favorites view for quick access.
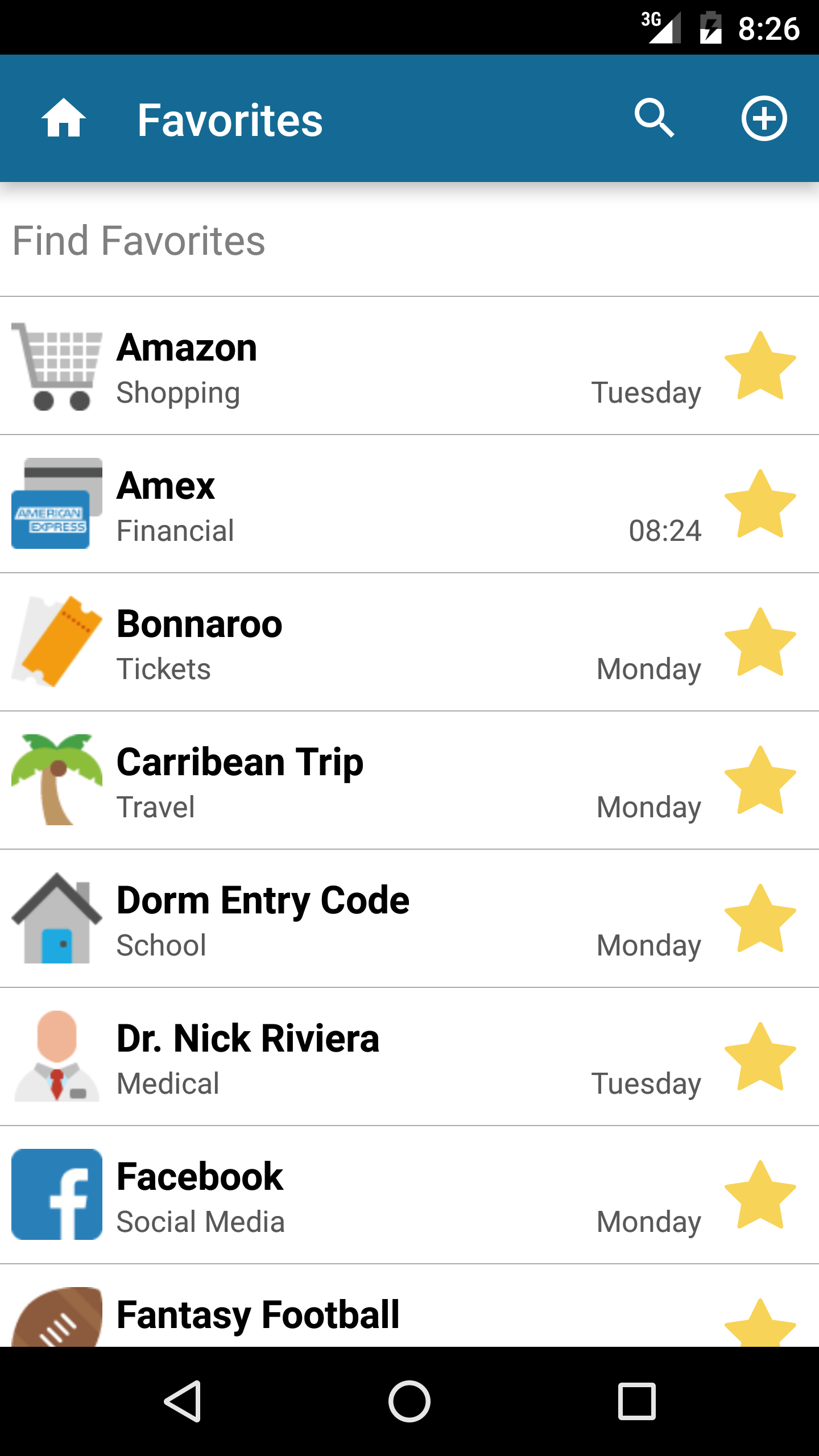
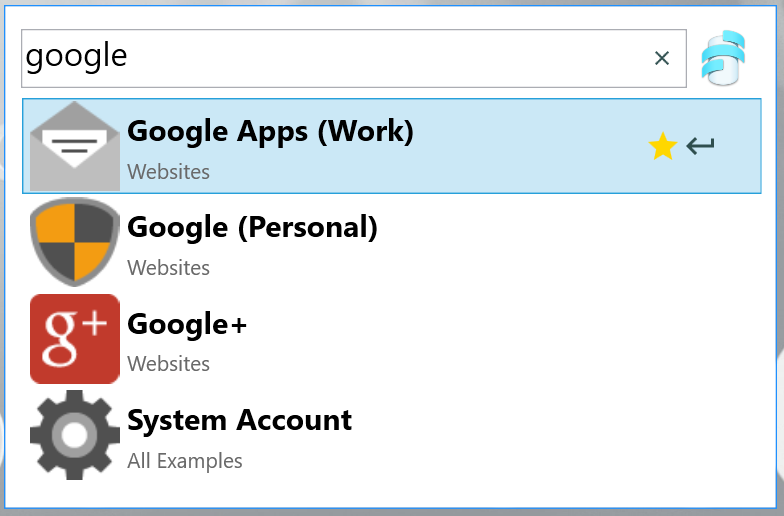
Favorites automatically sort to the top of search results, both within the standard search function and in Secret Agent on the desktop. This allows you to very quickly access your most critical information in Codebook at a moment’s notice.
Other Improvements
Codebook 3 is also packed with other enhancements, improvements, and numerous bug fixes for every supported platform.
Upgrade Notes
Upgrading to Codebook is really easy. On most platforms, you’ll just need to run the update and look for the new icon. On iOS, if you have auto-update enabled, you may already have it installed!
Explicit instructions for updating Codebook are available on the upgrade FAQ, but here is the short summary:
-
Please backup your mobile devices and desktop databases before upgrading, either via WiFi, Dropbox, or Google Drive!
-
After the upgrade, the old STRIP icon will be replaced with a new Codebook icon. If you can’t find STRIP, look for Codebook instead. All your data will remain intact.
-
When you log in to Codebook for the first time the database format will be updated. Due to database file and feature improvements, STRIP 2.x will not sync with Codebook. Therefore, you should plan to update all of your devices and applications to Codebook at around the same time.
Feedback and Support
We are here to help during this transition in case you have any questions or difficulties with the upgrade process. Don’t hesitate to contact us:
Finally, once you’ve had a chance to try Codebook, we’d really like to get your feedback about the new look and features.
2015-12-10 07:00:00 -0500

Following the release of the SQLCipher for Windows Universal Application Platform package, we have issued a major update to our SQLCipher packages on the Xamarin platform which now includes PCL support.
SQLCipher for Xamarin iOS and SQLCipher for Xamarin Android include two different client libraries for interfacing with a SQLCipher database. First, the Mono.Data.Sqlcipher library for data access with an ADO.NET style interface. We have recently replaced our second client library, previously based on sqlite-net with that of SQLite.Net.Core-PCL. While the new library maintains much of the same behavior as its predecessor, providing a light weight ORM, it is now PCL compatible. This will allow developers targeting both iOS and Android devices using the Xamarin platform to share much of their data model source code, minimizing duplication across platforms.
A sample below shows how quickly you can construct a secured SQLCipher database connection for your Xamarin iOS application.
var password = "SQLCipher!";
var documentsPath = Environment.GetFolderPath(Environment.SpecialFolder.Personal);
var libraryPath = Path.Combine(documentsPath, "..", "Library");
var databasePath = Path.Combine(libraryPath, "sqlcipher.db");
var conn = new SQLiteConnection(new SQLitePlatformIOS(password), databasePath);
If you are interested in giving either SQLCipher for Xamarin iOS, or SQLCipher for Xamarin Android a try, trials are available for both. Please feel to reach out if you have any questions.
2015-12-01 07:00:00 -0500
We are happy to announce the immediate availability of our commercial SQLCipher for Windows Universal Application Platform package, available for purchase here. We have previously supported both the Windows Runtime and Windows Phone platforms as separate component packages, however moving to the Windows 10 platform allows for a different approach. We will continue to support the older individual packages with updates to SQLCipher, however for developers looking to strictly target Windows 10 on the desktop, and/or Windows 10 Mobile we now have a unified package option.
Application Integration
The new package is bundled as a Visual Studio extension and local Nuget package. The client library itself uses the SQLite.Net.Core-PCL component providing a lightweight ORM interface. Utilizing a PCL component at the base allows for shared database logic between Windows 10 and Windows 10 Mobile projects, further simplifying the developers ability to target multiple platforms and minimize code duplication.
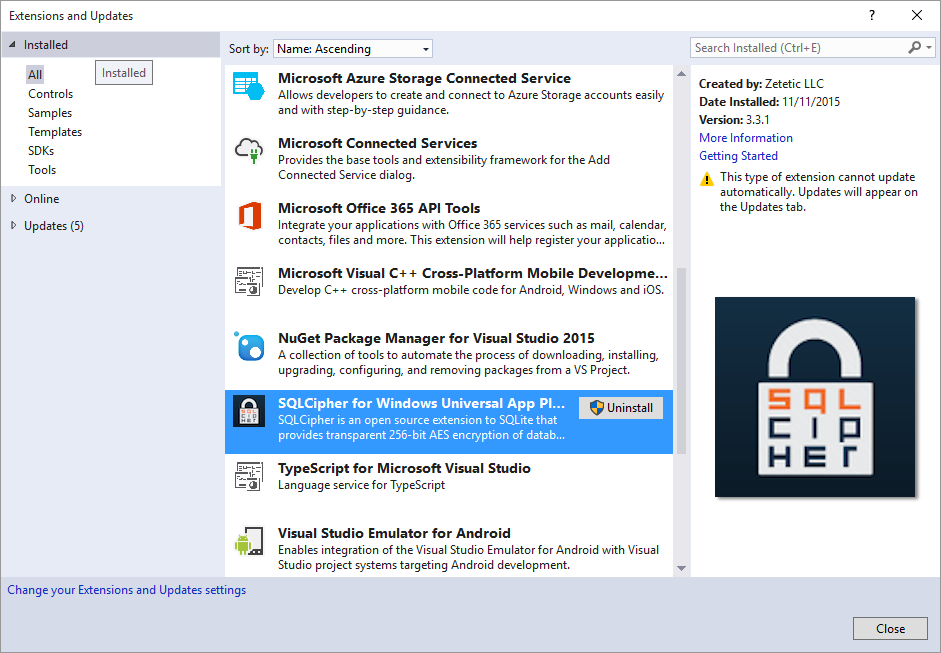
The component packaging includes precompiled binaries, documentation, and demos to allow for quick integration of new or existing projects wishing to protect their data. A sample below shows how quickly you can construct a secured SQLCipher database connection for your Windows 10, or Windows 10 Mobile application.
var key = "SQLCipher!";
var databaseFile = "test.db";
var databasePath = Path.Combine(ApplicationData.Current.LocalFolder.Path, databaseFile);
var connection = new SQLiteConnection(new SQLitePlatformWinRT(key), databasePath);
Please note, this new package requires usage of Visual Studio 2015. SQLCipher for Windows Universal Application Platform does not work within the Windows Phone 8.0/8.1 platforms, nor does it work on the Windows Runtime operating system; we offer separate packages for these environments. Please feel free to reach out to us if you have any questions.








