2013-11-12 09:46:26 -0500
This morning we've released STRIP 2.1.0 for all versions of STRIP in the various App Stores and made it available via auto-update in the desktop apps. This version of STRIP includes a major security upgrade and is not backwards compatible or sync compatible with earlier versions of STRIP. Thus, you should be prepared to upgrade all copies, and please back up your data before proceeding.
Important Upgrade Notes
Instructions for updating each STRIP are available on our FAQ.
- Please backup your mobile devices and desktop databases before upgrading, either via WiFi, Dropbox, or Google Drive.
- When you log in to STRIP 2.1.0 for the first time the database format will be updated. Due to database file and feature improvements, STRIP 2.1.0 will not sync with earlier versions of STRIP. Therefore, you should plan to update all of your devices and applications to STRIP 2.1.0 at around the same time. More information is available on our upgrade FAQ.
What's New
STRIP 2.1.0 features our updated SQLCipher encryption engine, and increases the number of PBKDF2 iterations used to derive your database key from 4,000 to 64,000, providing substantial security gains against increasingly sophisticated brute-force attacks.
STRIP for Android
- Increases PBKDF2 iterations from 4,000 to 64,000
- Upgrades SQLCipher to version 3.0.0
- On the fly searching - search as you type
- Sync with other copies of STRIP requires minimum version of 2.1.0
STRIP for Windows
- Increases PBKDF2 iterations from 4,000 to 64,000
- Upgrades SQLCipher to version 3.0.0
- Sync with other copies of STRIP requires minimum version of 2.1.0
- Fixes ObjectDisposedException during data import
STRIP for OS X
- Increases PBKDF2 iterations from 4,000 to 64,000
- Upgrades SQLCipher to version 3.0.0
- Sync with other copies of STRIP requires minimum version of 2.1.0
- Fixes erroneous caching of field value heights on record view
- Fixes truncation of long notes in view
- Adds a Choose button to password generator view, corrects value copy into editor
- Fixes masking of newly created fields after editing is completed
- Auto-lock timer now stores setting in the encrypted database to prevent tampering
- Adds preference to lock STRIP on start of screensaver and screen lock
STRIP for iOS
- Increases PBKDF2 iterations from 4,000 to 64,000
- Upgrades SQLCipher to version 3.0.0
- Sync with other copies of STRIP requires minimum version of 2.1.0
- Uses Apple's CommonCrypto for hardware-accelerated cryptography
- Fixes crash adding date fields on iPad version
- Prompts for current password before allowing password reset
- Fixes appearance of "Export Data..." button on Lite version
- Changes minimum supported OS to iOS 5.0 for iPhone versions (still 6.1 on iPad)
2013-11-11 17:14:25 -0500
We're excited to announce that SQLCipher 3 is now available. This release includes several substantial improvements:
- New default key derivation iteration count of 64,000, a 16x PBKDF2 work factor increase over the previous version
- New PRAGMA cipher_migrate, a simple utility command to upgrade an existing 1.x or 2x. database in place
- New sqlite3_key_v2 and sqlite3_rekey_v2 functions to allow keying and rekeying of named databases
- New ATTACH behavior, requiring an explicit key to be passed for encrypted databases
- Extended Raw Key/Salt feature, making it possible to set both the encryption key and database salt via a raw key specification
- Based on SQLite 3.8.0.2, a recent stable release of SQLite
Detailed notes about the differences are available in the original SQLCipher 3 beta announcement post.
It's important to note that these key derivation changes enable a much higher level of security than previous versions though, by default, SQLCipher 3 will not open older database. To enable backwards-compatibility, it is possible to adjust settings at runtime or migrate older databases:
- To open an older database using SQLCipher 3, set the KDF iterations back to the old value of 4000 using PRAGMA kdf_iter = 4000
- To attach and export data to a new database, use the sqlcipher_export() convenience function
- To migrate and upgrade an existing database in place, use the new PRAGMA cipher_migrate feature
Finally, as a result of the increased key derivation count, users may notice that opening and keying a database takes longer in SQLCipher 3 than with previous release. Noticeable performance issues can almost always be avoided by ensuring that applications do not frequently open and close connections. That said, while we strongly recommend using the new default KDF settings, it is possible to set the default back to 4,000 iterations before any databases are open by calling the global PRAGMA cipher_default_kdf_iter = 4000; before invoking the SQLCipher library.
The latest source code can be found in the official project repository, and SQLCipher Commercial Edition libraries are already available in the SQLCipher Store. Commercial edition customers with CipherCare may contact us with their original order number for details on how to download an update.
Please take a look, try out the new library changes, and let us know if you have any feedback. Thanks!
2013-10-31 13:16:42 -0400
STRIP is our password manager—we put a lot of love and work into it, we want it to be as secure and easy to use as possible, we really want it to be the best password manager out there. But we don't usually publish our long-term plans because we like to set our own timelines and we don't want to over-promise and under-deliver. STRIP is a pretty big project, involving four native applications that sync together, so our planning process is quite careful and iterative. This can give the impression that we're moving slowly when we're actually doing a ton of work behind the scenes. Since folks are asking a lot lately, we'd like to tell you about the next version of STRIP, and provide some insight on where we're going from here.
STRIP 2.1.0
The next, soon to be released version of STRIP for all platforms is version 2.1.0. We've been testing it all summer alongside a major update to our encryption engine SQLCipher. We're preparing the iOS and Mac versions for app store review now and hope to release all versions simultaneously (including Windows and Android) as soon as we're approved for release. This version will be available for free to upgrading customers.
Here's what you should know about STRIP 2.1.0:
- It increases the number of PBKDF2 SHA-1 iterations used to protect your database key from 4,000 to 64,000
- We believe this change is critical to protecting our customers from increasingly sophisticated attacks
- It is not backwards compatible, once the database is upgraded it cannot be used with older versions
- It will not sync with earlier versions of STRIP, you'll need to upgrade STRIP on all your devices
- It's important that you upgrade to this version for future compatibility
This change to your encrypted database is an enormous gain in security at a time when powerful, well-funded organizations as well as individuals and researchers are developing sophisticated means for attacking encryption systems, and in particular brute-forcing passwords. With computing power increasing rapidly it is time to make attacks on STRIP's encryption literally more expensive, massively so.
Some additional things to note about the iOS and OS X versions:
- iOS versions now use Apple's CommonCrypto library for hardware-accelerated encryption
- The iPhone version supports iOS 5 up to iOS 7
- The iPad version supports iOS 6.1 up to iOS 7
- The OS X version supports OS X 10.6 up to OS X 10.9
We had to drop support for iOS 4.3 finally, because CommonCrypto hardware acceleration support is not available to us there, and it's absolutely necessary due to the increase in PBKDF2 iterations on the database key. Hopefully anybody still running 4.3 out there has the ability to upgrade to the latest iOS. We realize that's not everybody, but numbers suggest there are very few folks in that position, and we do have a contingency plan for anyone who does (if that description fits you, please get in touch with us soon.)
It's important that you upgrade to 2.1
Device and sync compatibility are really important to us and minimizing disruption is best for our customers. In STRIP 2.2 we won't be changing the database format again, but we may start changing the minimum supported OS versions of the various apps as we seek to improve them and take advantage of new APIs. This means that STRIP 2.1 running on older devices that either can't upgrade STRIP to 2.2 or can't upgrade to the latest version of their OS in order to upgrade will remain sync-compatible with STRIP 2.2, allowing us to proceed with needed enhancements without leaving customers on 2.1 out in the cold.
That's why we think you should upgrade as soon as possible, once STRIP 2.1 is released. We've been testing this upgrade for many months to make sure we've got it right, and we'll be standing by to help if there are any issues.
STRIP for iPhone and iPad version 2.2
STRIP for iPhone and STRIP for iPad are going to get face-lifts for iOS 7, we're working on them now and we think you're really going to enjoy the change, it's already a pleasure for us as we work on it, make changes, and test. Here's a sneak peak at the Sync screen in progress:
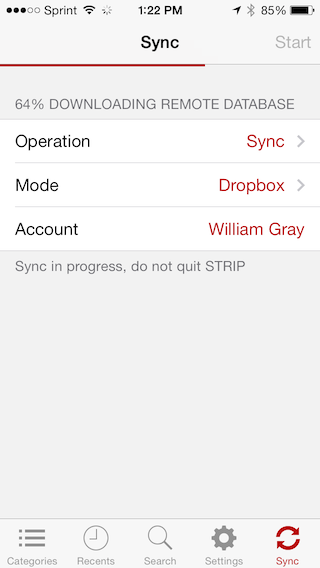
Work in progress, not final by any means
We're revisiting all of our interfaces as we go over them, to see if we can do a better job, and that was certainly the case for the Sync view. I always wanted to provide better indicators of current sync status. Not only is it a pleasure to watch the red-tinted progress bar zoom across the screen, this will be a big help when debugging issues with our customers by providing them with more information.
This version will also be available for free to upgrading customers.
What's Next
Image and media storage is one of our biggest and oldest feature requests, and we've already done some proof-of-concept work there. It presents challenges in speed and efficiency when it comes to sync operations. Another of our biggest feature requests is background sync—it should just work. And the other biggest feature request is sharing databases—allowing you to decide which of your data you share with whom, with seamless synchronization of your records. The magic word here is sync.
These are not easy problems to solve well and we want to make sure we get it right in the experience department, in making STRIP as easy to use as possible while providing these great new features. On top of that, we need to make sure we maintain and improve the high level of security and diligence our customers have hopefully come to expect from us. Putting aside the interface changes, what we need is a new sync system. We think solving these problems together is critical to providing the best version of STRIP yet, and work is already underway. We call it STRIP 3 and it's pretty much where we've always wanted to take the app, ever since we launched as a stand-alone app on the iPhone.
Beta Testing
Want to help us make STRIP better? Please consider joining our beta testing program. We're looking for testers who are excited to run the latest betas as we go forward, test with (backed up) real-world data, and provide lots of feedback. If that sounds like you, please get in touch!
2013-10-30 14:22:11 -0400
This is a quick post about STRIP, our password manager, and how you can use it to make life a little easier. Say you have a Foo Web Services account and you run virtual machine instances there—you'd typically store three pieces of information in STRIP so that you can log into the console and access your instances:
- username
- password
- web browser console login URL
Thus when you need to log in, you can just pull up STRIP, start typing the record name, quickly copy the password and then double click on the URL to launch it in your browser to get going:
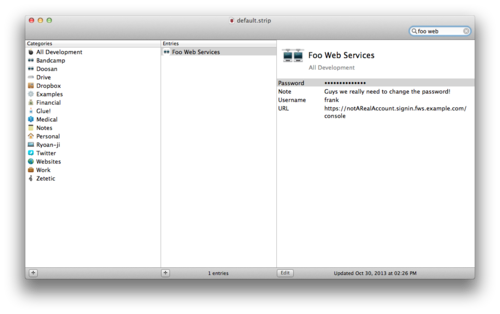
Okay, nothing new there, right? But maybe the reason you're logging in to the Foo Web Services console is because you need to get the DNS names for your virtual machine instances so you can log in to one or more of those servers via SSH. Now it's a nuisance, now you have to copy each URL out of the web interface and into your Terminal.
But STRIP can take care of this for you, cutting out the step to your web console, by using URL fields. Let's create a new label just to make clear what's going on here by going to the File menu and selecting Customize Labels, which produces a sheet showing all your labels in STRIP:
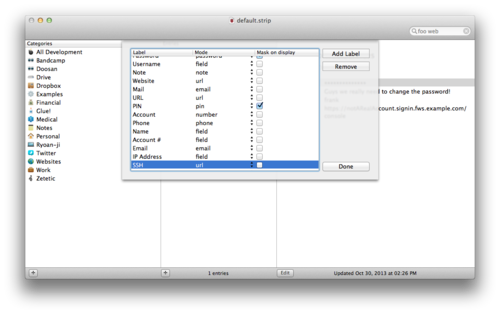
Create a new label, name it SSH for now, and set the Mode to "url," then click Done to dismiss the Customize Labels sheet.
In our Foo Web Services record we'll add a new field for each of our virtual machine instances, setting the label to SSH for each. If we use the SSH URL connection string format in the field itself, ssh://user:password@hostname:port, we'll be able to double-click these fields to launch SSH connections in Terminal (or the preferred SSH app/client on your computer/device). In the following screen, I've added two such SSH urls:
- ssh://frank@ec2-not-a-real-node1.compute-0.fws.example.com
- ssh://frank@ec2-not-a-real-node2.compute-0.fws.example.com
Now when I double-click these fields on the record in STRIP my operating system offers to launch to launch Terminal for me (with a warning, I should add):
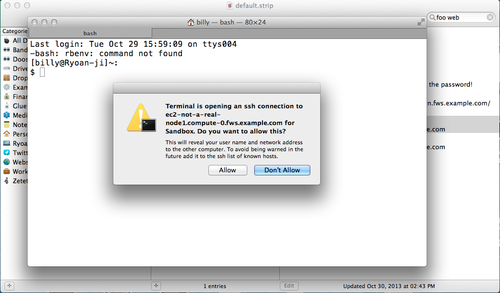
After I click Allow, a new Terminal window launches and fires up an SSH connection so I can do whatever I normally do to verify my identity (password login, public key, etc).
This also works on iOS or Android if you have an SSH client installed. Simply tap on the URL fields in STRIP for iOS or Android to get the option to launch the URL in your preferred SSH app:
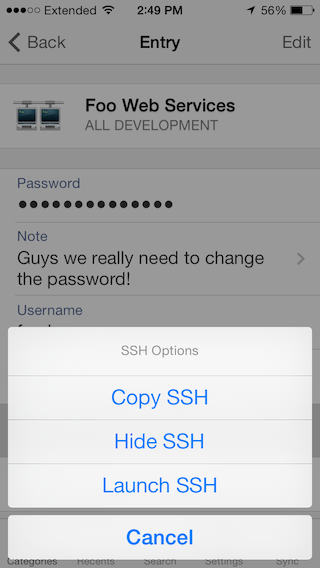
(Yes, that's a sneak preview of the iOS 7 interface, don't hold us to it, work in progess!)
When I tap on Launch SSH, iOS opens up an app on my device that's registered for handling ssh: connections, in this case it's good old TouchTerm:
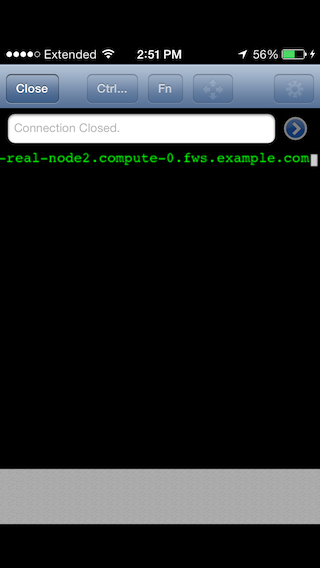
As you can see, TouchTerm attempts to open the connection with the details supplied in the URL string (and in the case of example.com, gives up for good reason).
Creating labels with a mode of url is a powerful way to make it easy for you top pop into STRIP and fire up a connection to a system that requires credentials you've stored in STRIP.
Off-topic: have a favorite SSH client for iOS or Android that we should check out? Feel free to leave comments!
2013-09-22 13:10:13 -0400
We've become aware of a compatibility issue with STRIP running on iOS 7 that is affecting users who switch between the numeric and text keyboards during login. The problem occurs when toggling between the "abc" and "123" modes while the Mask on. When switching between keyboard modes with the application switch, the contents of the password entry box is cleared. If you don't realize that the password box has been cleared, this have the appearance of being unable to log in following on iOS 7.
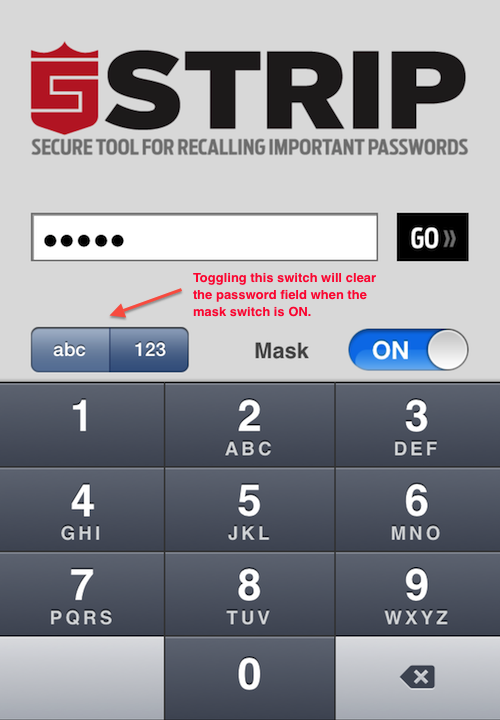
For example, with a mixed password of "6789abcd", one might start off in the numeric entry mode to enter the first part of the password. However, under iOS 7, if one were to tap the "abc" toggle to switch into the standard keyboard mode to enter the remainder of the password, the contents of the password field would be cleared, removing the 6789 from the password text field. A user who didn't notice this could continue entering text, but only "abcd" would be passed into STRIP, resulting in an incorrect password error.
The good news is that there are two simple workarounds for this issue that will allow you to log into STRIP:
- Our recommended approach is to use only the "abc" mode to log in for the time being. To do this, switch the mode to "abc", then tap the "123" button in the bottom left corner of the iOS keyboard to bring up the numeric keyboard. The numbers will be arranged across the top of the keyboard. Enter any digits, then tap the "ABC" button on the bottom left of the keyboard to toggle back to text.
- If you are in a secure location where other people can't observe your screen, toggle the "Keep password hidden" switch to "off". While the Mask switch is off the keyboard toggle will operate normally.
We are treating this as a high priority issue and will make sure there is a fix for this issue in the next release of STRIP. Please contact us at support@zetetic.net if you have any questions or other issues.





