STRIP, Keychain, and XARA
A customer wrote us regarding recent reports of vulnerabilities to the Keychain in iOS and OS X and whether or not these affect STRIP password manager:
Is STRIP for iOS vulnerable to this “0 days flaw” in Apple software and allows “cross-app resource access (XARA) attacks”? Is the password for the iOS STRIP app stored in the keychain of the iOS or anywhere else in the iOS system other than in the STRIP app itself?
STRIP does not store the user’s master password in the iOS or OS X Keychain (back to this in a moment).
However, STRIP makes use of the Dropbox and Google-supplied frameworks for authenticating against their services for sync if you choose either of these sync modes. Both of those frameworks store the OAUTH authentication credential in the iOS and OS X Keychains (open Keychain Access on your Mac and search for “STRIP” to have a look).
Touch ID Authentication on iOS
In the soon-to-be-released version of STRIP for iPhone and for iPad we’ve added the oft-requested feature of Touch ID login. This feature is completely optional, disabled by default, and only available on devices with Touch ID. The feature works by storing your master password for STRIP encrypted in the Secure Enclave on the device, through the Keychain.
Are these Keychain items vulnerable to attack?
It depends. There’s a great article on iMore.com explaining the attacks and what’s vulnerable (emphasis theirs):
Contrary to what some reports have said, while a malicious app cannot read your existing keychain entries, it can delete existing keychain entries, and it can create new keychain entries that are readable and writeable by other, legitimate apps. This means a malicious app can effectively trick other apps into saving all new password entries to a keychain it controls, and then can read.
iOS is unaffected:
The researchers note that one of the reasons iOS is unaffected by this is that iOS doesn’t have ACLs (access control lists) for keychain entries. Keychain items on iOS may only be accessed by an app with a matching bundle ID, or group bundle ID (for shared keychain items). If a malicious app created a keychain item that it owned, it would be inaccessible by any other app, making it entirely useless as any sort of honeypot.
Using the Touch ID login feature in the next version of STRIP for iPhone and iPad should not leave you vulnerable to this exploit.
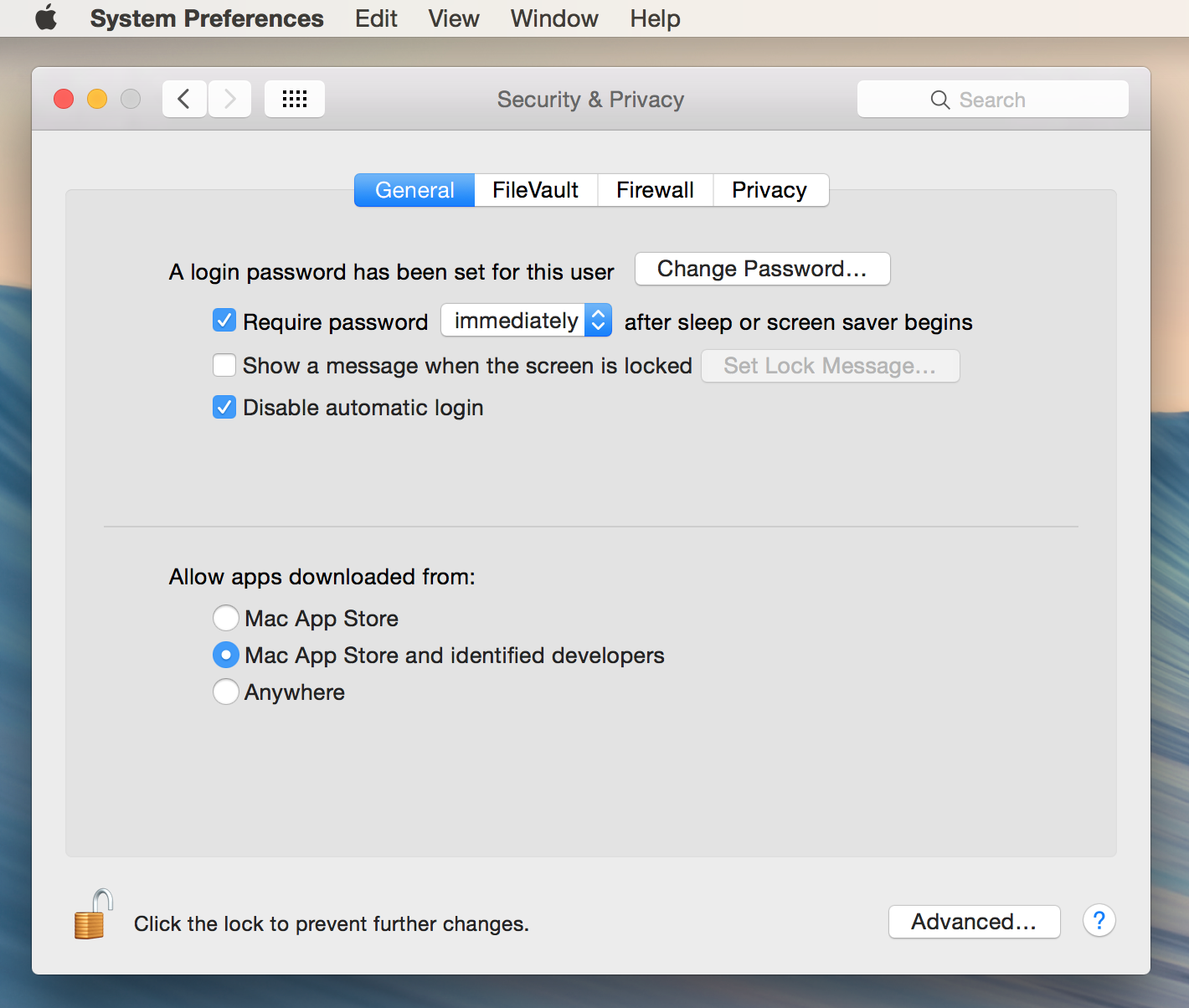
In the end you always want to avoid suspicious, maliciously crafted software; once a host operating system is compromised it becomes very difficult to keep your data secure. Watch out for phishing attacks, where email is crafted to trick you into visiting a malicious website or downloading malware posing as normal attachments. On OS X you can limit the apps allowed to run on your Mac to those signed by Apple or by Apple-identified developers (like Zetetic):
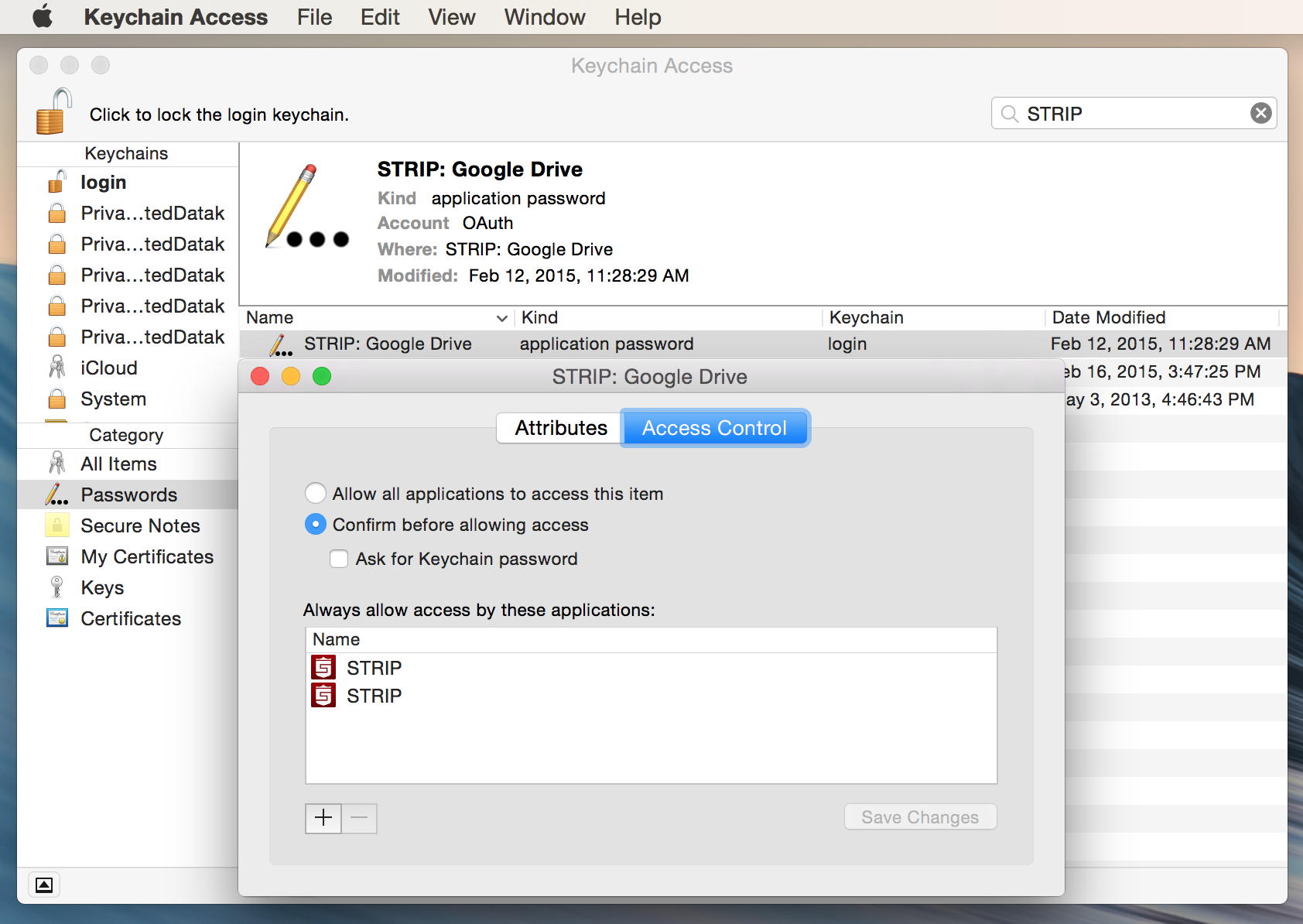
If you are concerned about malicious keychain entries you can check for them easily:
- Open Keychain Access
- Search for “STRIP”
- Select the Keychain item in the right pane and select File -> Get Info (or type command+i)
- Select Access Control
- In the list of allowed applications you should only see STRIP
What about WebSockets?
While STRIP on the Mac provides a utility function for looking up your passwords and inserting them in other applications, it does not include a browser plugin and makes no use of WebSockets, another point of vulnerability detailed in the recently announced exploits.
blog comments powered by Disqus