2012-03-20 09:26:48 -0400
During the third day of the BlackHatEU conference, Andrey Belenko and Dmitry Sklyarov of ElcomSoft presented an analysis of iOS and Blackberry password managers entitled “Secure Password Managers” and “Military-Grade Encryption” on Smartphones: Oh, Really?. It was a complete analysis of 17 of the most popular password management programs showing that many password managers store data in an unencrypted format, "encrypted so poorly that they can be recovered instantly", or are susceptible to basic cracking techniques.
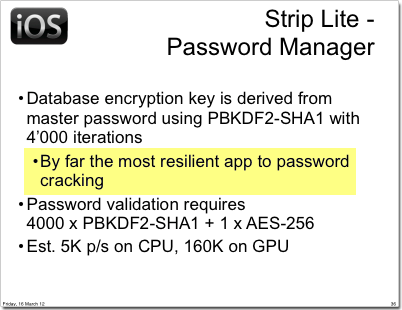 One of the apps reviewed in the paper was Zetetic's Strip Lite, which is backed entirely by SQLCipher. As such, the results of their findings hold true for all apps using SQLCipher. From the reports we've heard it was noted as the one exception that properly implemented strong cryptography, was "by far the most resilient app to password cracking", and the most secure app for iOS.
One of the apps reviewed in the paper was Zetetic's Strip Lite, which is backed entirely by SQLCipher. As such, the results of their findings hold true for all apps using SQLCipher. From the reports we've heard it was noted as the one exception that properly implemented strong cryptography, was "by far the most resilient app to password cracking", and the most secure app for iOS.
However, the paper includes some brute force cracking estimates that serve as an important reminder about the need to use a strong passphrase when encrypting data. Their estimates show clearly that given suitably fast GPUs it would be possible to brute force standard numeric PIN numbers due to their low entropy / small search space.
This topic has been discussed exhaustively on the SQLCipher mailing list in the past, but the security of SQLCipher is highly dependent on the security of the key used. Even though we take great pains to increase the difficulty of brute force attacks using PBKDF2, and avoid dictionary / rainbow table attacks with the per database salt, these techniques can only be successful if a suitably strong key is chosen.
The original whitepaper contains all of the source information, and you can also read more about our initial thoughs on the analysis.
2012-03-18 16:52:50 -0400
Update 3/21/2012: We've released a graphical tool for Windows and OS X called Convert to Strip since we published this article. It's for converting your SplashID (or 1Password) data to STRIP's CSV format, read about and download Convert To Strip here.
At BlackHatEU last week, ElcomSoft presented a paper where they demonstrated attacks on several popular Password Managers. One of the most critical flaws was identified in SplashID, a popular password manager for iOS. The researchers found that a global key was used to encrypt the master password, rendering it instantly recoverable. A working exploit has already been published.
In light of this critical problem, there has been some interest from prospective customers in migrating to STRIP, which was recognized at the same conference as the "most resilient to password cracking" and one of the only applications that properly implemented strong cryptography.
To help support migration of users from SplashID to Strip, we we developed this conversion script that can run through the SplashID file and create a CSV file that you can import into STRIP Desktop or the free StripSync helper app. The following example assumes some familiarity with the Terminal app for OS X, that the SplashID export file is named "SplashID Export.vid," and that it's in the same directory as the Ruby script.
Note: There is now a free conversion tool available for windows too!.
0. Download the script and save it to your Desktop
Download this zip file containing convert.rb and expand it. Copy the convert.rb file to your Desktop.
1. Export the SplashID data
Launch SplashID Safe and login. Once the application is unlocked, go to the File menu and select Export, then SplashID vID.
On the panel that appears (below) select Export all records, and un-check Export Attachments. Keep the suggested name for the file, click on Where to select your Desktop, and then Save. When prompted, enter a blank password.

2. Convert the data
Open the Terminal.app and enter the following commands:
cd ~/Desktop
ruby convertb.rb
You should see output similar to the following:
$ ruby convert.rb
Examining SplashID Export.vid...
We've found 11 entries, composing output...
Your file strip-import.csv is ready for import into STRIP!
3. Check the data
There is now a 'strip-import.csv' file on your Desktop. You can open it in a spreadsheet editor to check its contents (e.g. OpenOffice.org, Numbers, Excel), or open it in a simple text editor. It's always a good idea to check the data over before importing it into STRIP.

In my case, since I already had data in STRIP, I set the Category to "SplashID Data" in the spreadsheet for each row so that all the new entries would show up together in the next step.
4. Import the data into STRIP
Log into STRIP, go to the File menu, and select "Import...", and choose the strip-import.csv file on your Desktop.

Once you've checked that everything looks OK in strip you should delete the two plaintext import/export files and remember to securely empty your trash.
2012-03-16 16:29:51 -0400
During the third day of the BlackHatEU conference, Andrey Belenko and Dmitry Sklyarov of ElcomSoft presented an impressive analysis of iOS and Blackberry password managers entitled “Secure Password Managers” and “Military-Grade Encryption” on Smartphones: Oh, Really?.
The results are shocking: of the 17 password management programs analyzed, they showed that most of the products, including many of today's most popular password managers, are either:
- storing data in an unencrypted format,
- "encrypted so poorly that they can be recovered instantly"; or
- susceptible to basic cracking techniques (i.e. rainbow tables)
The sole exception in the study was our own password manager, Strip, backed by SQLCipher.
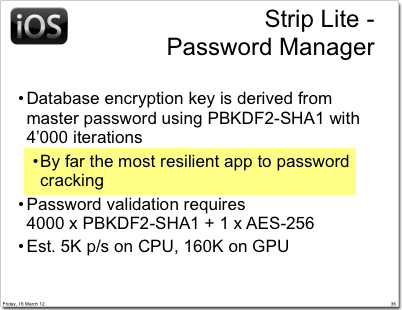
The presenters noted that Strip, using an encryption key derived through 4,000 iterations of PBKDF2-SHA1 was "by far the most resiliant app to password cracking" and appeared to be the only application that properly implemented strong cryptography. We're pleased that ElcomSoft found Strip to be a solid implementation, and that it was noted as the most secure App during the presentation.
It's important to note, however, that the detailed cracking analysis found in their white paper provides an excellent demonstration of the need to use a secure master password. Given the enormous power of today's CPU and GPUs it is possible to attempt an attack on a weak passphrase, even though key derivation protects against rainbow tables and slows down brute force searches. ElcomSoft's estimations show that using a powerful GPU it would be possible to try every combination numeric passwords in a short period of time.
Keeping that in mind, Strip's security really comes down to the security of your passphrase. Use a long alphanumeric passphrase with a combination of upper case, lowercase, digits, and metacharacters. For comparison, the calculations presented in the ElcomSoft paper yield that an 8 character random ASCII password for Strip and SQLCipher would take an estimated 1,315 years to crack.
If you're interested in reading more about the types of attacks and security issues with these sorts of application's please check out the excellent source presentation and whitepaper. Likewise, if you're interested in moving to a mobile password manager with a higher level of security than the rest, you should take a look at Strip.
2012-03-15 11:55:35 -0400
Monitoring a large Active Directory and Windows environment with Zetetic Combine can turn up some interesting things... in this case we took a look at a Combine beta program participant's administrative password reset activity over the last few weeks.
It's a colorful chart, and a long one! Over 50 distinct support and administrative folks have been helping locked-out users around the globe. Of course, it's always good policy to make sure the people exercising these rights are doing so properly... all the more reason to implement good security log collection and analysis policies.
(The names have been obscured to protect the innocent, as well as the mostly-innocent.)
2012-03-14 13:13:20 -0400

At Zetetic we do a lot of work for our clients with Microsoft's identity management stack: Active Directory, AD Federation Services, Forefront Identity Manager 2010, and its predecessors Identity Lifecycle Manager 2007 and Microsoft Identity Integration Server 2003. FIM is a great tool, but--perhaps unsurprisingly--its connector to Lotus Notes has always come up a bit short because:
- It can only talk to the Domino Names and Address Book with predefined fields and behaviors
- It's limited to exactly one running Notes management agent (MA) at a time
- It has a tendency to crash the FIM Synchronization Service, usually requiring a reboot, when the Notes API gets out of whack
- Microsoft only officially supports a few legacy versions of the Notes client and server
(It's also impossible to prevent the standard Notes MA from complaining about replication-save conflicts or incomplete records, which then foul up the delta import process, but I digress...)
Having worked for years in the Notes and Domino development arena before switching full-time to C#, it seemed only natural to build a MA that bridges the gap between the many, many real-world business uses of Notes databases and FIM / ILM, while at the same time keeping the large, complex Notes client API out of the FIM server process.
Our solution to this problem is a two-parter:
1. A backend Windows service that manages all native access to the Notes API, and exposes a facade of Notes sessions, databases, documents, and the Notes Certification Authority, via .NET 2 TCP Remoting, and,
2. An Extensible MA for FIM / ILM that communicates with the .NET Remoting service to implement FIM's import and export operations.
The result is a FIM agent that uses only .NET managed code, moving all the native Notes stuff into a separate process--or even better, a separate host. Upgrading or moving FIM then no longer means dealing with the Notes client, or whether the 64-bit FIM process will have trouble with 32-bit Notes, or even trying to find the older editions of Notes that the FIM product supports.
We think this solution is an ideal fit for any FIM / ILM customer with Notes business databases or identity infrastructure in their environment because it greatly extends FIM's reach to read and update Notes databases, while also providing a serious boost in reliability. It's tremendously useful for application and messaging migration, easy to set up, and we provide full support to get your FIM to Notes and Domino integration configured and running.
For more information: Zetetic Management Agent for IBM Lotus Notes and Domino
 One of the apps reviewed in the paper was Zetetic's Strip Lite, which is backed entirely by SQLCipher. As such, the results of their findings hold true for all apps using SQLCipher. From the reports we've heard it was noted as the one exception that properly implemented strong cryptography, was "by far the most resilient app to password cracking", and the most secure app for iOS.
One of the apps reviewed in the paper was Zetetic's Strip Lite, which is backed entirely by SQLCipher. As such, the results of their findings hold true for all apps using SQLCipher. From the reports we've heard it was noted as the one exception that properly implemented strong cryptography, was "by far the most resilient app to password cracking", and the most secure app for iOS.




