SQLCipher at the BlackHatEU ElcomSoft Presentation
During the third day of the BlackHatEU conference, Andrey Belenko and Dmitry Sklyarov of ElcomSoft presented an analysis of iOS and Blackberry password managers entitled “Secure Password Managers” and “Military-Grade Encryption” on Smartphones: Oh, Really?. It was a complete analysis of 17 of the most popular password management programs showing that many password managers store data in an unencrypted format, "encrypted so poorly that they can be recovered instantly", or are susceptible to basic cracking techniques.
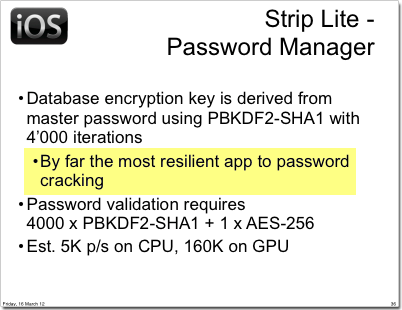 One of the apps reviewed in the paper was Zetetic's Strip Lite, which is backed entirely by SQLCipher. As such, the results of their findings hold true for all apps using SQLCipher. From the reports we've heard it was noted as the one exception that properly implemented strong cryptography, was "by far the most resilient app to password cracking", and the most secure app for iOS.
One of the apps reviewed in the paper was Zetetic's Strip Lite, which is backed entirely by SQLCipher. As such, the results of their findings hold true for all apps using SQLCipher. From the reports we've heard it was noted as the one exception that properly implemented strong cryptography, was "by far the most resilient app to password cracking", and the most secure app for iOS.
However, the paper includes some brute force cracking estimates that serve as an important reminder about the need to use a strong passphrase when encrypting data. Their estimates show clearly that given suitably fast GPUs it would be possible to brute force standard numeric PIN numbers due to their low entropy / small search space.
This topic has been discussed exhaustively on the SQLCipher mailing list in the past, but the security of SQLCipher is highly dependent on the security of the key used. Even though we take great pains to increase the difficulty of brute force attacks using PBKDF2, and avoid dictionary / rainbow table attacks with the per database salt, these techniques can only be successful if a suitably strong key is chosen.
The original whitepaper contains all of the source information, and you can also read more about our initial thoughs on the analysis.