2014-03-31 12:27:49 -0400
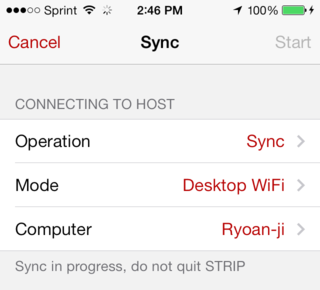
We released a point update for STRIP for iPhone and STRIP for iPad today alongside today's update to STRIP for OS X. The new versions contain various bug fixes and a handy new improvement: a cancel button on the Sync view. STRIP for iPhone and STRIP for iPad are available now in the iTunes App Store (if you don't see 2.2.2 yet try again in a few minutes, the App Store doesn't always get the update out quickly after we Release.)
Changelog
- New Button to Cancel sync in progress
- Fixes direct IP / Hostname view for WiFi Sync
- Fixes masking switch on Note labels
- Fixes login interface on device rotation
- Fixes crash on resume when menu showing on iPad
If you're enjoying the changes we've been making or if you'd like to see more, please consider reviewing STRIP in the iTunes App Store and letting us know. If you have any issues whatsoever or if you'd prefer to get in touch with us directly please write us at support@zetetic.net. Thanks!
2014-03-31 11:55:49 -0400
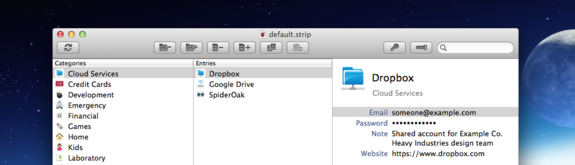
Today we released STRIP for OS X 2.2.0, a major improvement over 2.1.0 in terms of stability, resource utilization and convenience. If you take a look at the image above you'll see some new additions to the interface—toolbar buttons! The icons for these were lovingly designed by Jory Raphael at SensibleWorld.com, and we'll be seeing more artwork from Jory in STRIP soon.
OS X 10.9 Mavericks Required
This version of STRIP requires a minimum OS X version of 10.9 Mavericks, do not install it without first upgrading OS X. STRIP for OS X 2.2.0 is sync-compatible with the previous version 2.1.0 allowing some time to upgrade, but with all the fixes in this update we're hoping you'll make the leap with us sooner than later.
Download
Download STRIP for OS X from the Mac App Store. If you purchased the independent build of STRIP for OS X from Zetetic, simply launch the app and select "Check for Updates" from the STRIP menu in the menu bar if you are not prompted to update.
What's New
Toolbar: We probably should have added these buttons a lot sooner, but hopefully this is a reasonable initial set with obvious functionality. One of the buttons however, with the flashlight icon, does something new. This button (and the associated keyboard combo shift+command+M) allows you to quickly show and hide all masked fields on the entry view and we find ourselves using this all the time now.
Entry view: There's so much we have planned here but for now a minor update to the display of field labels and values along with a slew of fixes for the actions presented in the context menu when you right-click on a field (in view and edit modes).
Import: If you've ever tried to import a lot of records into STRIP for OS X via CSV (like say 500), it was very slow, consumed a ton of memory and was prone to crashing. All fixed up! Although, there is a hard limit of 998 records in one import at the moment. We'll be looking to fix that in future updates.
Memory use: Such memory leaks, many fixes. We'll be paying a lot more attention to this from here on out, making heavy use of profiling tools to manage resource utilization and ensure STRIP is a good citizen on the OS.
Sync: Some bug fixes here as well, along with a fully functional Cancel button. Sometimes there are errors on sync or the network connection is interrupted—you need to be able to cancel the operation and STRIP should handle errors gracefully.
Guts: We found some ugly bugs in how STRIP handled data persistence and put a lot of effort into fixing that up. We're constantly trying to improve and here's one area where we couldn't ignore code written three years ago. There will be no bit-rot in STRIP!
As always, if you have any questions or issues please contact us at support@zetetic.net. If you like this update to STRIP and want to see more please consider leaving a rating or a review in the Mac App Store, tell us what you'd like to see next.
Changelog
- Adds new timer to erase field values copied to clipboard after 2 minutes
- Now uses internal, private pasteboard for copying category and entry records
- Adds preference to sort labels alphabetically (defaults to enabled)
- Adds new toolbar buttons
- Adds Start Sync button to toolbar
- Adds Password Generator button to toolbar
- Restores global availability of Password Generator (shift+command+P)
- Adds new show/hide all masked fields feature to toolbar and View menu (shift+command+M)
- Adds right-click and keyboard command to launch selected field (command+return)
- Adds shift+command+J for masking and revealing the selected field
- Adds 4 and 8 hour intervals to preferences for Auto-lock
- Includes minor improvements to entry view display
- Fixes crash during import
- Fixes poor/slow performance during import
- Fixes memory leaks during import
- Fixes memory leaks in main window interface
- Fixes Auto-lock engaging during import for lengthy imports and shorter lock intervals
- Fixes sync failure regression on passwords with a single-quote character
- Fixes window restore location after Auto-lock
- Fixes preventing access to Preferences window while locked
- Fixes right-click commands on fields improperly mapped to selected row instead of click target
- Fixes sorting of new and edited category and entry records to maintain alphabetic sort
- Fixes any missing or duplicate replica IDs on sync
- Fixes dysfunctional cancel button on sync progress sheet
2014-03-19 14:54:54 -0400
WhatsApp, a popular cross platform messaging application, has been in the news recently, not only for the high-profile acquisition from Facebook, but also due to security concerns. A recently published article disclosed the WhatsApp database is exposed to third-party access and is not properly secured.
The Issues
The published analysis showed that WhatsApp can store both plain-text and encrypted databases on the SD card, where they could be accessed by malicious 3rd party applications. The only protection for the database is a simple AES cipher with an easily derived key, which leads to real security issues.
Because the database is encrypted as a whole, it’s very likely that at some point during application usage, the entire database itself must exist somewhere in a plain text form in order for the SQLite library to use it. This could pose a risk if the raw data became available to an attacker.
However, the most significant issue is that WhatsApp uses easily discoverable keys on the the encrypted database. Originally a static key was used to perform the encryption on all Android installations, though WhatsApp has now been updated to use a derived key based on the name of the email account on the device. In either case, this renders the encryption key available to applications running on the device, allowing exploits.
A Note on Key Management
Key management is a difficult issue, requiring careful consideration during application design. Storing the key directly within the application, or derived solely based on data on the device, is a poor practice. Decompiling a binary to access the key or determine the process used to create it is a rather straight forward process. Once the key has been identified, the data is at risk.
We strongly recommend that applications ensure that key data is provided by the user (e.g. a user supplied password). It’s fine to combine that with with device data to generate a password, but that is an additional precaution. It’s equally important to pass the key material through a key derivation function with a salt in to generate the actual key for encryption. This helps protect against dictionary and brute force attacks.
How SQLCipher Could Help
In the case of WhatsApp, SQLCipher can help address some of the factors above by providing a more secure environment for application data. Coupled with a user-supplied password or pin, SQLCipher’s built in security controls would automatically provide key derivation and encryption using a unique per-database salt. This would ensure that even if two databases are created with the same password they will not have the same encryption key. Furthermore, using SQLCipher, data is only decrypted as needed, decreasing the risk of plain-text data exposure. Finally, using SQLCipher would provide additional security features to ensure the integrity of the data, preventing tampering and closing off other potential attack vectors.
Many companies both small and large depend on SQLCipher to protect their data across a variety of platforms. Because WhatsApp is already using SQLite to store data, converting to use SQLCipher in its place would require minimal modifications, something WhatsApp might consider.
2014-02-22 15:27:36 -0500
If you weren't already aware, Apple released iOS update 7.0.6 yesterday to patch a hole in their use of SSL/TLS that could allow an attacker to compromise encrypted communications. If you haven't updated your iOS devices you'll want to do so as soon as possible. A little bird tells me OS X updates are on the way next week, although I imagine that's no surprise and I've seen it speculated elsewhere.
There's a great explanation of the bug here by Adam Langley, but I'd like to point out an interesting comment by John Gruber on Daring Fireball where he links to Langley's post:
I don’t want to start a coding-style war, but I think this bug would not have happened if the code had been written using curly braces after the if statements.
I think there's no doubt about that. A little while ago I gave up my stubborn use of BSD-style in my C and Objective-C code and now wherever I see it I cringe a little and then go about fixing it up to be more "proper" in my mind. It's a nuisance, but worth it. For some time now, I think perhaps at the recommendation of Zed Shaw in his online book Learn C the Hard Way, I've been making sure to always use braces to encapsulate anything depending on an if statement or other conditional to avoid scenarios like the one that caused Apple's exploit. Other rules I now keep are no more braces on the next line, and avoiding blank lines. This gist should give a good example of what I mean, even though it's a bit silly:
I even use braces to encapsulate the branches of switch statements these days! I like to zap blank lines because I think it forces me to review code more closely; it's harder to skim and encourages me to keep things nice and DRY.
A minor aside: Learn C the Hard Way is really great even if you know C already. Worth a couple of hours, it's a fun read and good for tightening up your skills.
Update: I also avoid assignment operators in if statements, and I tend to keep conditional expressions very explicit. This way I know what in my code above, self.fugeez is a BOOL, or returns that type. If I want to check that a pointer is nil, then if (self.fugeez == nil), not if (self.fugeez). If I want to test that my BOOL fugeez is false, then if (self.fugeez == NO), an explicit comparison. Just makes it easier to see what's going on later. I'm not quite as religious about this, but I'm trying to stick to it and adjust where I see my old ways.
2014-02-17 14:39:01 -0500
As a follow-up to the original Zetetic.Security library that adds PBKDF2 and BCrypt-based HashAlgorithms to .NET, we're pleased to announce the release of Zetetic.Security 1.1.0.0, which provides options for greater work factors when generating password hashes.
The original hash implementations use 5,000 rounds of PBKDF2, and a BCrypt work factor of 10^10. The 1.1 release adds support for 64,000, 128,000, and 256,000 rounds of PBKDF2, and BCrypt work factors from 10^11 to 10^16. As before, the best way to use these hash algorithms is by installing Zetetic.Security to the Global Assembly Cache, and updating machine.config to register the new classes. (Hint: you can find the path to the effective machine.config file in System.Runtime.InteropServices.RuntimeEnvironment.SystemConfigurationFile).
Once installed and registered, the new HashAlgorithms can be used in code as per the following sample (I wrote this one in LinqPad for simplicity's sake):
Of course, bear in mind two important caveats before updating your applications to use any new password hashing strategies:
1. .NET MembershipProviders don't have any way to know what HashAlgorithm generated any particular user's hashed password in storage. Therefore, changing the hash algorithm will cause your users' logins to fail until they reset their passwords.
2. A stronger hashing algorithm is likely to eat up significantly more CPU cycles. Plan accordingly so that applying 10^16 rounds of BCrypt doesn't open the door to a denial-of-service attack (or blow your AWS or Azure budget!).
Download from Github
View on NuGet

