STRIP for Android stores sensitive information, which may cause some to pause when they see the permissions required to run the application on their Android devices. STRIP for Android requires access to the Internet, access to your Google accounts, and telephone permissions to name a few. We would like to clarify the need for those permissions, and in doing so, explain a feature available in STRIP for those unaware.
STRIP for Android provides a mechanism when long tapping on any given field to allow you to perform context-specific actions on the data you store. For example, if you long tap on a URL, STRIP for Android will offer to launch that URL in a browser. Likewise, if you have a telephone number stored, a long tap will offer to dial that number for you. You can think of it as a quick action feature associated to the data you store, should you wish to invoke it. With regard to account access, that is to allow STRIP access to your Google Drive account, should you wish to perform backups/synchronize your data to your Google Drive account. That said, we do not make phone calls without your request, we also do not access your account information without your permission. An example of the context sensitive menu within STRIP for Android is shown below.
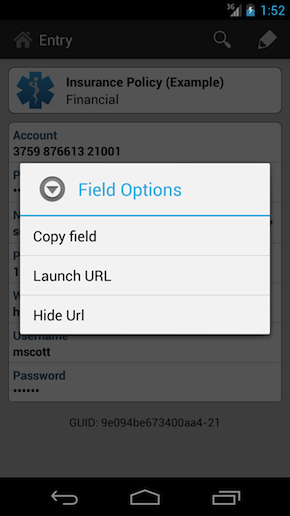
With this, we hope you can use the quick action features within STRIP to streamline your experience within the application when accessing your information.
This morning we're excited to pull the switch on two important updates to STRIP for Android and OS X. STRIP for Android is carrying numerous bug fixes we've been working on for a while and a new full-screen theme. STRIP for OS X has been updated to fix the previously noted data persistence bug and is now quite a bit more robust in that department.
To get the latest:
We've tracked down an ugly little bug in the latest update of STRIP for OS X, 2.2.0, involving data persistence for newly added or edited fields on entry records. While the bug itself has one main root due to a recent change in STRIP's plumbing, it can be demonstrated in a couple of ways outlined below. These bugs can be worked around and we have a bugfix release 2.2.1 in the App Store review pipeline now. With any luck we'll have the update in the Mac App Store next week.
Avoiding Data Loss
To edit a record in STRIP the customers clicks on the Edit button (or command+E) to begin editing. Edits to field values are not being saved immediately, but are being delayed until the user again clicks on Edit. Therein lies a good deal of the problem. If the customer chooses to then launch Sync before ending editing, or uses the "Create new label" feature the field values get whacked and are lost.
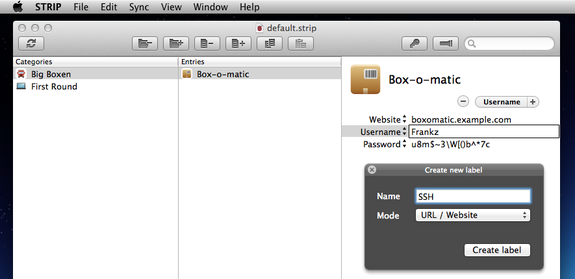
To avoid any data loss with STRIP 2.2.0 for OS X avoid using the Create new label feature until we get 2.2.1 out, and remember to end editing by clicking on the Edit button to ensure your chanages are saved. You can add new labels in the interim by going to the File menu and selecting Customize Labels.
STRIP 2.2.1 ensures edits are persisted to the encrypted database immediately as before. We apologize for the oversight, it's an embarassing bug.
If you would be interested in joining our private STRIP for OS X beta group, which will provide you with early access builds, please contact us at support@zetetic.net.
Like most service and software providers, we've been working hard at Zetetic to assess the impact for our customers resulting from this week's OpenSSL security disclosure, commonly known as the OpenSSL Heartbleed bug. More specifically referred to as CVE-2014-0160, this issue has undermined the security of many internet platforms by allowing attackers to read arbitrary memory from services using the popular OpenSSL library to provide secure communications over the web. This attack can allow extraction of private keys, session data, and user information from affected websites.
STRIP, SQLCipher, and OpenSSL
Users of the STRIP Password Manager may recall that the application uses Zetetic's SQLCipher encrypted database library to protect all underlying application data. While SQLCipher does make use of OpenSSL, it only relies on low-level encryption interfaces. Since there is no use of OpenSSL's SSL functions, there is nothing that would expose SQLCipher or STRIP to direct attack via Heartbleed. More details on the use of OpenSSL in SQLCipher are available separately in our Heartbleed Security Statement for SQLCipher.
As a result, we're pleased to report that users who currently rely on STRIP for their data security need not be concerned with Heartbleed exposure on their local computers and devices a result of the software.
STRIP Cloud Sync
It's important to note that STRIP does provide a variety of optional synchronization features that use cloud services like Dropbox and Google Drive. Both of those services used affected versions of OpenSSL in the past, and may have been vulnerable to the Heartbleed bug.
STRIP's synchronization features do keep copies of the encrypted STRIP data on the cloud service. However, STRIP is very careful never to expose any unencrypted data to cloud services during synchronization. All STRIP data stored in Dropbox or Google Drive is fully encrypted using a strong encryption key derived from your master password.
While there haven't been any public reports of attackers using Heartbleed against Google or Dropbox, the nature of the bug make it possible that data on those services could have accessed without knowledge. However, since the database is fully encrypted at rest using STRIP, there is no risk of plaintext data exposure.
Recommendations
Even with STRIP's advanced protections, this is a really good time to review the strength of your master password, because STRIP's security really comes down to the security of your passphrase.
We recommend using an alphanumeric passphrase with a combination of upper case, lowercase, digits, and meta-characters of the maximum length possible to allow for convenient entry.
If you are currently using a weak password, especially in combination with Cloud sync, we'd strongly recommend that you change your STRIP password now to ensure the long term security of your data.
Finally, many internet sites have been affected by the Heartbleed bug, and are issuing statements suggesting that users change their passwords, log out of mobile applications, and reset authentication tokens, etc. Please take these notices seriously and update your credentials for affected systems as soon as possible.
We take security seriously and we are happy to communicate with customers about the details of this issue, or how to take appropriate action, so please don't hesitate to contact us if you have any questions.
Like most service and software providers, we've been working hard at Zetetic to assess the impact for our customers resulting from this week's OpenSSL security disclosure, commonly known as the OpenSSL Heartbleed bug. More specifically referred to as CVE-2014-0160, this issue has undermined the security of many internet platforms by allowing attackers to read arbitrary memory from services using the popular OpenSSL library to provide secure communications over the web. This attack can allow extraction of private keys, session data, and user information from affected websites.
We are pleased to report that SQLCipher is not directly impacted by the Heartbleed bug and subsequent disclosure. Many SQLCipher platforms, including SQLCipher for Mac OS X, Android, Xamarin.Android, ADO.NET, and Windows C++ do make extensive use of OpenSSL. However, they only utilize the low level "libcrypto" interfaces to access encryption algorithms. Specifically, SQLCipher's OpenSSL provider uses the EVP interfaces, random number generator, and PKCS5_PBKDF2_HMAC_SHA1. There is no use of OpenSSL's SSL functions, and thus nothing that would expose SQLCipher to direct attack via Heartbleed.
As a result, applications that currently rely on SQLCipher for local data security need not be concerned with Heartbleed exposure as a result of the SQLCipher library. Of course, application and service providers should be sure to carefully audit their software and infrastructure to ensure that there aren't other components or services that rely on affected versions of OpenSSL.
Finally, even though Heartbleed does not impact SQLCipher, we will include the latest OpenSSL 1.0.1g in upcoming releases of SQLCipher Commercial Edition for those customers using our commercially supported libraries to ensure dependency on the latest stable version.
We take security seriously and we are happy to communicate with customers about the details of this issue, so please don't hesitate to contact us if you have any questions.

