2023-04-27 08:00:00 -0400
We are pleased to announce that SQLCipher 4.5.4 is now available. It includes the following notable changes:
SQLCipher Core
- Updates baseline to use SQLite 3.41.2
- When using an OpenSSL cryptographic provider,
PRAGMA cipher_provider_version will return the version loaded at runtime instead of at compile time
- Improves guarding against cryptographic provider initialization failure
- A new encrypted database which is
ATTACHed as the first operation after keying the main database will have the same salt as main database
- CocoaPods minimum platform versions are now iOS 11.0, macOS 10.13, tvOS 11.0, and watchOS 7.0
SQLCipher Android
- Breaking Change: Android Database SQLite Exception classes are now used for compatibility with Android Support and Room. All SQLCipher exception classes have been removed. All Android users should adjust their code to import the appropriate exceptions from
android.database.* and android.database.sqlite.* after upgrading.
- Breaking Change: Updates android.sqlitex dependency to version 2.2.0. Integrators should adjust the
dependencies block in build.gradle accordingly.
- Breaking Change: Minimum supported SDK version updated to 21 on 32 bit platforms for compatibility with upstream SQLite changes
- Fix issue where the use of an incorrect encryption key could be mistakenly identified as database corruption
- All builds updated to use latest LTS version
r25c
SQLCipher Commercial and Enterprise
There are a large number of enhancements to the Commercial and Enterprise packages for this release:
- Breaking Change: Android packages have been renamed to remove the
-release suffix from .aar files. Integrators should adjust the dependencies block in build.gradle accordingly.
- Improves .NET MAUI support targeting iOS and Android to avoid legacy Xamarin dependencies
- Improves and allows multi target support for Maui and Legacy Xamarin
- Updates NuGet packages to remove deprecated features
- Linux packages now support distributions with older glibc versions (>=2.17) including RedHat 7 and Centos 7
- Adds new example projects for SQLCipher for Android packages
- Removes Windows 8.1 support from SQLCipher for Cordova (platform is no longer supported by Microsoft)
- non-FIPS packages using OpenSSL now include 1.1.1t, except Windows UAP which uses OpenSSL 1.1.1s
- Enables Fortify Source for OpenSSL on older Android platforms
- Updates to sqlite-net 1.8.116 as baseline for the zetetic-sqlite-net-core package
- Updates SQLitePCL.raw dependencies for all .NET packages to version 2.1.4
- SQLCipher for JDBC now uses xerial/sqlite-jdbc release 3.41.2.1 as baseline
Availability
Commercial and Enterprise - On-demand access to new releases of SQLCipher packages are available to all licensees with an active support subscription from the Customer Downloads fulfillment site. Licensees will also receive a separate email notification regarding the update and can contact us at any time for private support directly from the SQLCipher development team.
Community Edition - SQLCipher Community Edition source code is available on GitHub, via AAR packaging for Android, and CocoaPods for iOS.
2022-12-19 07:00:00 -0500
We are pleased to announce that SQLCipher 4.5.3 is now available. It includes the following noteable changes:
SQLCipher Core
- Updates baseline to use SQLite 3.39.4
SQLCipher Commercial and Enterprise
There are a large number of enhancements to the Commercial and Enterprise packages for this release:
- Enables support for the REGXEP operator
- Introduces new built in math functions
- Improves support for .NET Maui to include cross platform single-project app support for Windows, macOS (Catalyst), iOS, and Android (including a reference application)
- Updates .NET example applications to target latest .NET Core LTS, Microsoft.Data.Sqlite.Core, Microsoft.EntityFrameworkCore.Sqlite.Core, and SQLitePCL.raw
- Removes armv7 and armv7s architectures for iOS and targets SDK 11 to support Xcode 14
- Renames packages from
sqlcipher-xamarin-ios and sqlcipher-xamarin-android to sqlcipher-ios-net and sqlcipher-android-net respectively (Xamarin is still supported, this change is only to avoid naming confusion)
- Updates non-FIPS packages using OpenSSL to 1.1.1s
- Updates SQLitePCL.raw dependencies to version 2.1.3
- Updates System.Data.SQLite baseline to version 1.0.117
- Updates JDBC baseline to latest release Important Note: For applications using the JDBC driver, previously the built-in
log() function computed the natural logarithm, but it now computes base-10 logarithm
Deprecation Notice: SQLCipher for Cordova 4.5.3 will be the last version to support Windows 8.1. Due to the upcoming end of extended support by Microsoft it will not be included in future releases.
Availability
Commercial and Enterprise - On-demand access to new releases of SQLCipher packages are available to all licensees with an active support subscription from the Customer Downloads fulfillment site. Licensees will also receive a separate email notification regarding the update and can contact us at any time for private support directly from the SQLCipher development team.
Community Edition - SQLCipher Community Edition source code is available on GitHub, via AAR packaging for Android, and CocoaPods for iOS.
2022-08-03 08:00:00 -0400
We are pleased to announce that SQLCipher 4.5.2 is now available. It includes the following major changes:
SQLCipher Core
- Updates baseline to use SQLite 3.39.2. IMPORTANT: This version includes an upstream SQLite fix for CVE-2022-35737. We recommend any applications dealing with large string inputs (> 2GB) upgrade to the latest release.
- Fixes issue where
PRAGMA cipher_memory_security could report OFF when it was actually ON
- Fixes unfreed allocation leak when using OpenSSL version 3.x
- Simplifies OpenSSL multi-version conditional code
- Adds support for building against recent versions of BoringSSL
- Initial public beta release for the new SQLCipher for Android Refresh
SQLCipher Commercial and Enterprise
The following changes and enhancements are available for Commercial and Enterprise packages:
- Java and .NET library wrappers have been updated to the latest available versions.
- non-FIPS packages using OpenSSL now include the latest release of 1.1.1q
- Fixes linking for .NET MAUI iOS targets
Availability
Commercial and Enterprise - On-demand access to new releases of SQLCipher packages are available to all licensees with an active support subscription from the Customer Downloads fulfillment site. Licensees will also receive a separate email notification regarding the update and can contact us at any time for private support directly from the SQLCipher development team.
Community Edition - SQLCipher Community Edition source code is available on GitHub, via AAR packaging for Android, and CocoaPods for iOS.
2022-05-11 08:00:00 -0400
We are excited to announce the beta availability of a new version of SQLCipher For Android. This new release provides major benefits including optimized support for concurrent database access, drastic performance improvements, API simplification, and codebase modernization. With the new library SQL operations are executed on a ThreadLocal<SQLiteSession> instance which completely eliminates the aggressive locking behavior that could occur with the original version of SQLCipher For Android. Built-in WAL journal mode and connection pooling allows for parallel execution of queries from multiple threads. The updated Java API, based on the android.database package found in the AndroidBindings project, eliminates virtually all dated legacy code from the project.
History
We would like to thank Signal for helping to support the development of this new library which will benefit Android developers everywhere. SQLCipher For Android was initially released over 10 years ago following initial work with Guardian Project, making the security provided by SQLCipher available on the Android ecosystem. A lot has changed over the years; Zetetic continues to maintain the library, integrating new versions of SQLCipher, adding support for 64-bit device architectures, adding Room/Support API integration (thanks commonsguy!), and improving the project integration experience to name a few. SQLCipher For Android was based on an older version of the android.database.sqlite Java API. Unfortunately, this limited the abilities of the library, specifically in terms of concurrency. The new version of the library builds on the solid foundation of SQLCipher for Android with an eye toward concurrency at the forefront.
Availability
As SQLCipher for Android receives downloads in the hundreds of thousands every year, we are taking a safe and measured approach to revising the library; providing stability for developers who depend on the security of SQLCipher is paramount. Zetetic will continue to maintain the original SQLCipher For Android library for some time until the refresh may be considered a full replacement. Initially, the new library will be available in source-only format (available here); developers will need to provide both the SQLCipher amalgamation and OpenSSL dependencies to evaluate the library while we are in a preview state. Eventually, we will publish Community edition AAR artifacts. Commercial and Enterprise SQLCipher customers may access prerelease builds of the new SQLCipher for Android library from the Customer Downloads fulfillment site. While we are releasing the software in preview mode for now, the library is fairly stable and is already in use in on millions of devices with great success.
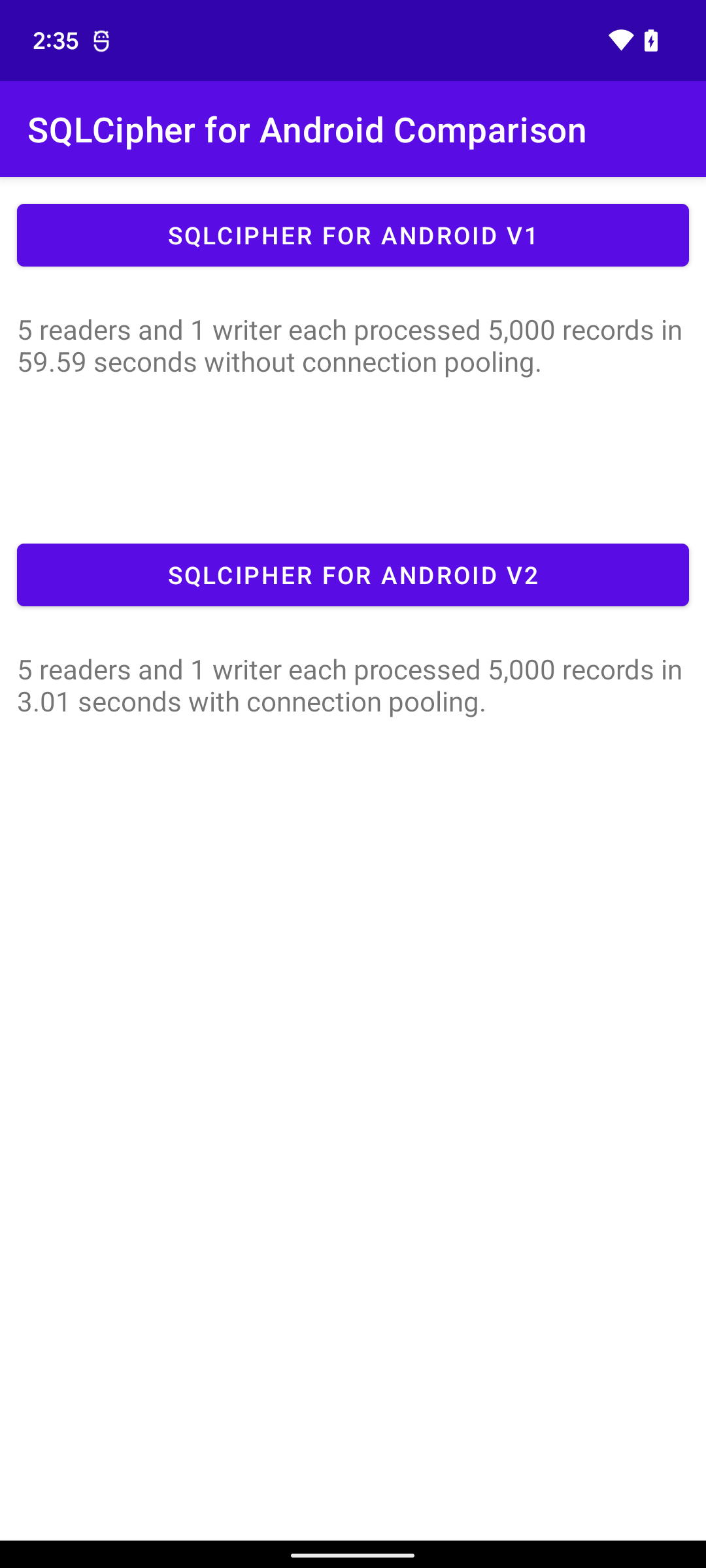
To provide some context around the performance difference between the old and new versions of SQLCipher for Android we prepared a small application that bundles both versions of the library and performs a series of multithreaded operations. The scenario represents a single writer operation producing 5,000 records. Concurrently, we have 5 separate reader operations running in separate threads attempting to individually read all data produced by the writer. The old (current) version of SQLCipher for Android took 59.59 seconds to process all records on a Pixel 6 device. The new version was able to complete the same task in 3.01 seconds. We look forward to hearing your feedback regarding the new library as we prepare to continue our support of SQLCipher for Android in the future.
2022-03-03 07:00:00 -0500
We are pleased to announce that SQLCipher 4.5.1 is now available. It includes the following major changes:
SQLCipher Core
- Updates baseline to use SQLite 3.37.2. IMPORTANT: This version includes an upstream SQLite fix for a database corruption bug. The bug could cause corruption when using
SAVEPOINT operations. We recommend any applications using SAVEPOINT upgrade to the latest release.
- Adds new
PRAGMA cipher_log and cipher_log_level features to allow logging of TRACE, DEBUG, INFO, WARN, and ERROR messages to stdout, stderr, file, or logcat
- Modifies
PRAGMA cipher_profile to use sqlite3_trace_v2 and adds a logcat target for Android
- Updates OpenSSL provider to support the
EVP_MAC API with version 3+
- Allows
PRAGMA cipher_integrity_check to work properly with databases larger than 2GB
- Fixes a missing munlock-before-free bug causing issues on some platforms
SQLCipher Commercial and Enterprise
The following changes and enhancements are available for Commercial and Enterprise packages:
- Significant optimizations to improve performance on all platforms
- Fixed issue that could cause excessively slow operation on Android emulators when using fast-boot
- Statistics collection is now disabled by default, but can be enabled with
PRAGMA cipher_stat_memory = ON and PRAGMA cipher_stat_crypto = ON.
- Java and .NET library wrappers have been updated to the latest available versions.
- non-FIPS packages using OpenSSL now include the latest release of 1.1.1m.
Availability
Commercial and Enterprise - On-demand access to new releases of SQLCipher packages are available to all licensees with an active support subscription from the Customer Downloads fulfillment site. Licensees will also receive a separate email notification regarding the update and can contact us at any time for private support directly from the SQLCipher development team.
Community Edition - SQLCipher Community Edition source code is available on GitHub, via AAR packaging for Android, and CocoaPods for iOS.
