2014-09-10 08:00:00 -0400
Many users interact with SQLCipher encrypted databases outside of application code for testing, database development, or troubleshooting. Yet until recently, we’ve only been able to recommend the use of the SQLCipher’s command line shell that is included in many of the SQLCipher Commercial Edition packages, or compiled under Community Edition distributions.
While powerful, many would prefer the experience of a native, graphical, desktop application instead of a command line shell tool, and we frequently receive inquiries about GUI tools that support SQLCipher.
For this reason, we are now very happy to announce that SQLiteManager, a popular and feature-rich database management studio from SQLabs, has released version 4.3.3 that adds native support for SQLCipher encrypted databases.
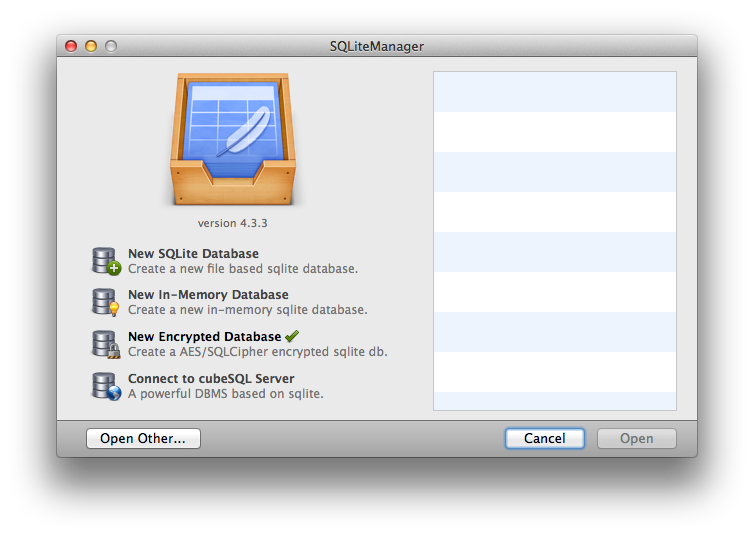
SQLiteManager provides a suite of advanced features for SQLCipher database management, including:
- Query execution
- Inline editing with syntax highlighting
- Table / schema editing
- Graphs and Charting
- Data import/export functions
- Support for both Windows and OS X.
If you need a user friendly and graphical interface for SQLCipher, please check out SQLiteManager today. Best of all, when you purchase SQLiteManager using the button below, you will help support the ongoing development of the SQLCipher project!
Buy SQLiteManager »
2014-09-05 07:00:00 -0400
Syncing with Dropbox or Google Drive from STRIP is pretty simple: you just select the sync method and kick off a sync. The first time you use the feature you’re prompted to login, but then STRIP does its thing.
However, apparent simplicity masks the steps STRIP takes to ensure that your data stays secure. So, what does STRIP do behind the scenes, exactly?
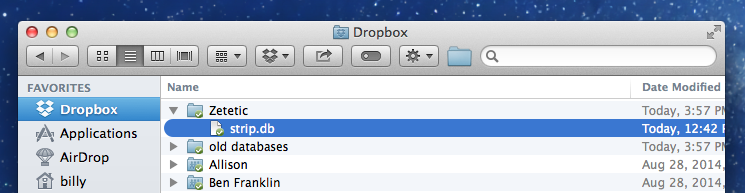
The very first time STRIP syncs with your cloud account it creates an encrypted replica of the local database on your device and pushes it up to the service.1 It places this file named strip.db in a folder named Zetetic. On each additional sync STRIP downloads this replica file, exchanges changes with it, and uploads it again, replacing the previous version. On both Dropbox and Google Drive older versions of this file are maintained by the cloud services’ individual file history features, meaning you have more than one backup to serve as convenient snapshots over time. No unencrypted data is ever stored in your cloud service by STRIP.
Here’s all that you should see in your Dropbox folder for STRIP after a sync:
Want to verify that strip.db is in fact an encrypted SQLCipher database and not a plain-text SQLite database, for instance? On OS X you can use hexdump from the Terminal app like so:
$ hexdump -C ~/Dropbox/Zetetic/strip.db
00000000 f0 b2 48 80 17 54 eb cd f0 92 28 8b e9 be cb 1b |..H..T....(.....|
00000010 d2 e6 f2 24 b5 68 b4 0f 62 ae b6 51 9a 35 8f e5 |...$.h..b..Q.5..|
00000020 2c f5 4a b4 7e fc 4b f4 20 f3 2a 24 a1 99 de 88 |,.J.~.K. .*$....|
00000030 95 d6 b3 a4 9a b4 78 ed 55 c3 2a 53 ed 3e f3 17 |......x.U.*S.>..|
00000040 8e 3b 6f 6c 0a 51 4b ce 0e 32 b0 73 0b 86 38 bf |.;ol.QK..2.s..8.|
00000050 9d ff 4a ab 65 68 aa 66 cf c3 d9 0c 47 3d 95 c3 |..J.eh.f....G=..|
00000060 12 e2 29 0d 92 7b 6c 24 d7 1f 62 a9 4c 8b b3 b2 |..)..{l$..b.L...|
00000070 a7 d3 04 9d 8d 5f ca 05 ed b5 33 5b 2e d6 d4 7d |....._....3[...}|
00000080 f6 1b f9 8c 24 ba e0 88 be a1 f3 8b 05 71 08 55 |....$........q.U|
...
Nothing but random-looking noise!
When the encrypted replica file is created it is initialized with the same password the user has set on the local, original database. STRIP uses SQLCipher for encryption, which provides strong key derivation:
When initialized with a passphrase SQLCipher derives the key data using PBKDF2 (e.g. OpenSSL’s PKCS5_PBKDF2_HMAC_SHA1 on some platforms.) Each database is initialized with a unique random salt in the first 16 bytes of the file. This salt is used for key derivation and it ensures that even if two databases are created using the same password, they will not have the same encryption key.
Key derviation helps protect against brute force and dictionary-based attacks, and in conjunction with a strong master password, provides the security necessary to take advantage of these cloud services. Remember that no cryptography can protect your data from a determined attacker if the master password is weak, or can be easily guessed in a brute-force or analytical attack on the database key, so choose wisely! We generally recommend users choose a reasonably long, randomized master password for STRIP, and completely avoid PIN numbers for security purposes.
STRIP’s sync system is bi-directional, meaning that changes from more than one replica or instance of STRIP can be exchanged on each sync. Thus you can sync STRIP on your Android, STRIP on your iPhone, and STRIP on your PC all against the same Dropbox or Google Drive account. One of the major advantages of syncing with these cloud services is that they operate over HTTPS, which is rarely blocked on most networks. This means as long as you have a network connection you can usually sync to make sure you’ve got the latest data on your device.
That’s really all there is to it!
Cloud-based synchronization certainly isn’t for everybody, and many people are naturally distrustful of Cloud security, but STRIP goes to great lengths to protect your data and make sure that unencrypted contents are never stored in third-party services.
We’ve tried to make the Sync feature in STRIP for the Dropbox and Google Drive cloud services as straight-forward and secure as possible. In the future, we’re planning to make synchronization even easier through a background service that doesn’t need to be initiated by the user. This is a problem we’re working on now, though we’re being careful to balance security and ease-of-use, since the two are sometimes at odds!2
1 Usually we use the provided API from Google or Dropbox with the exception of STRIP for Windows which simply places the replica strip.db file in your local Dropbox folder, with the expectation that the Dropbox sync client is running on that computer and will handle the upload accordingly.
2 Security researcher Dan Kaminsky has a really great article on this very topic that’s quite timely.
2014-08-27 06:00:00 -0400
We're very excited to announce the immediate availability of STRIP 2.4.0, along with a major new feature for OS X and Windows called Secret Agent. STRIP's Secret Agent adds a convenient way to quickly access your STRIP data from other Desktop applications. Today’s update also includes redesigned and new icons along with various bug fixes. Read on for more information!
Download
For instructions on updating STRIP please visit the updating STRIP FAQ in discuss.zetetic.net, our new community forum.
Note: Secret Agent is an advanced Desktop-based feature for STRIP for Windows and STRIP for OS X only. However, new versions for iOS and Android are also avaiable with new icons and bug fixes. If you're a mobile user and don't own STRIP for Windows or STRIP for OS X yet, please check them out. They are great desktop companions to the mobile applications!
Secret Agent
With a quick keyboard command you can now quickly and easily access your sensitive STRIP data for use in other applications on your Mac or Windows computer without having to switch apps, interrupt your flow, or copy and paste values.
How It Works
Secret Agent operates in the background on your computer, so it's available anytime. Once you’ve enabled Secret Agent in STRIP Preferences you can type a global hotkey command at any time to bring STRIP up from any application.
When you want to insert secure data into an active text field, for instance entering a website password into your favorite browser, press the hotkey and Secret Agent's search interface will appear, allowing you to quickly locate the record and field you need.
Searching for Data
Start with your cursor focused on an active text field in any application. Type Shift + Control + Backslash on Windows or Shift + Command + Backslash on OS X to bring up the Secret Agent interface. If STRIP isn’t currently unlocked you’ll see a login prompt. Once you’re at the search bar just start typing what you’re looking for:
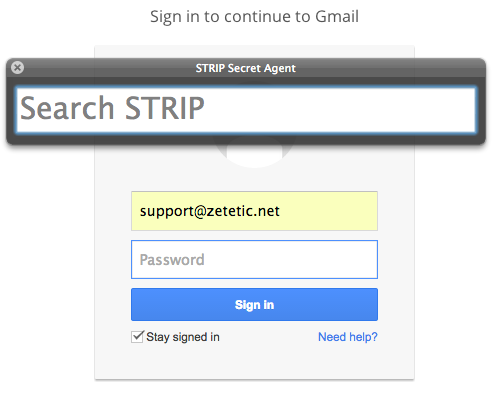
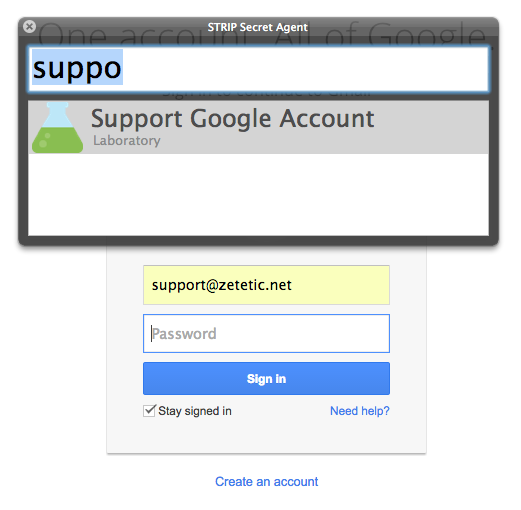
Once you locate the record you need, hit the enter key to bring up its detail view. Use the up and down arrow keys to navigate through the search results (or scroll and use your mouse, as you like.) While looking at the record detail in Secret Agent, arrow up or down to the field you want, then hit the enter key to automatically insert the field contents at the cursor location in the target application. Pressing the key combo again will bring the same record back up, making it easy to fill in multiple fields.
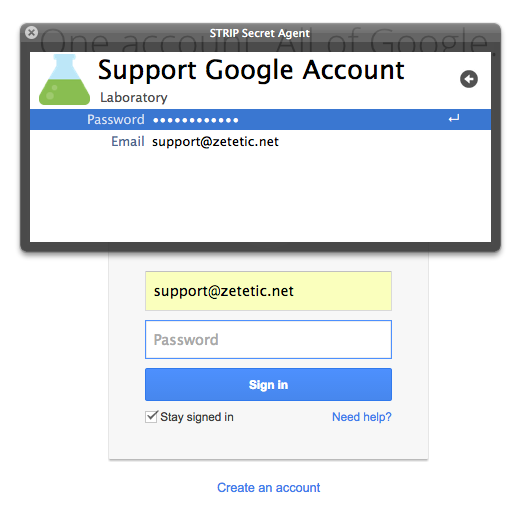
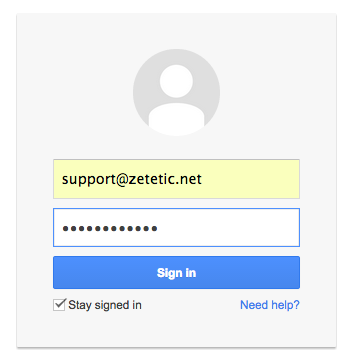
Secret Agent is a really fantastic and helpful addition to STRIP, providing easy access to data from any application. It's fast, keyboard driven, and most importantly, unlike some browser plugins or javascript-based integrations, Secret Agent is under your complete control. This minimizes concerns about malicious sites or applications stealing your data.
Redesigned and New Icons

One of the nicest visual improvements to the latest version of STRIP is the icons available to help you identify your categories and entries. We partnered with Jory Raphael at Sensible World design studio to completely redesign STRIP's entire icon collection, including the additon of sixty new icons created to our specifications. We couldn't be happier; they really make the app a pleasure to use. (Jory also designed the custom toolbar icons you see in STRIP for OS X and Windows!)
We're Here to Help
Please let us know if you have any questions about the upgrade process, how you like the new version, or if you run into any issues. We just launched a new community forum for STRIP at discuss.zetetic.net for discussion about the software. If you have a question or feedback about STRIP, please stop by, or send us an email to support@zetetic.net.
2014-08-13 10:28:37 -0400
If we've taken a little bit longer than usual to get back to you in the last week, it's because we had the great pleasure of attending PasswordsCon 14 in Las Vegas (and got into BSidesLV as well). Stephen and I presented "Enhancing Password Based Key Derivation Techniques" which focuses on two experimental developments in SQLCipher: adaptive key derivation and using hardware tokens. Billy presented "Password Generators & Extended Character Set Passwords," which was mostly an argument that it's time we started generating and using Unicode passwords.
There's an engaging sense of community at both of these conferences, and we had some really fun and interesting conversations with both the attendees and organizers. We would like to thank both Per Thorsheim and Jeremi Gosney, there is a lot of work involved in putting on a conference like this and they did an excellent job. Please find the slides to our presentations below, and don't hesitate to reach out if you have any questions or comments.
2014-06-17 14:02:53 -0400

While cranking out the updates for the 2.3 series of STRIP over the last few weeks (2.3.2 for iOS was just submitted to Apple this afternoon,) we've been hard at work on 2.4 for Windows and OS X, building a new feature we're really excited about. Want to help us test it, get early access to The New Thing™, find bugs, recommend improvements? We're on a tight schedule so we're hoping to find customers who are able give it some thorough use over the next couple of weeks and review the new feature. If that sounds like you, please write us! support@zetetic.net.







