How STRIP Syncs with Dropbox / Google Drive
Syncing with Dropbox or Google Drive from STRIP is pretty simple: you just select the sync method and kick off a sync. The first time you use the feature you’re prompted to login, but then STRIP does its thing.
However, apparent simplicity masks the steps STRIP takes to ensure that your data stays secure. So, what does STRIP do behind the scenes, exactly?
The very first time STRIP syncs with your cloud account it creates an encrypted replica of the local database on your device and pushes it up to the service.1 It places this file named strip.db in a folder named Zetetic. On each additional sync STRIP downloads this replica file, exchanges changes with it, and uploads it again, replacing the previous version. On both Dropbox and Google Drive older versions of this file are maintained by the cloud services’ individual file history features, meaning you have more than one backup to serve as convenient snapshots over time. No unencrypted data is ever stored in your cloud service by STRIP.
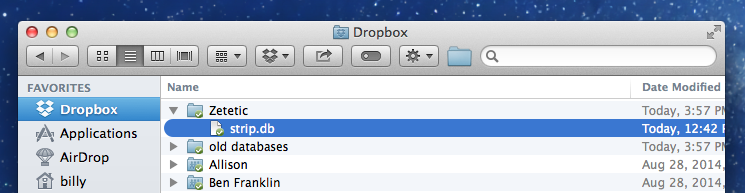
Here’s all that you should see in your Dropbox folder for STRIP after a sync:
Want to verify that strip.db is in fact an encrypted SQLCipher database and not a plain-text SQLite database, for instance? On OS X you can use hexdump from the Terminal app like so:
$ hexdump -C ~/Dropbox/Zetetic/strip.db
00000000 f0 b2 48 80 17 54 eb cd f0 92 28 8b e9 be cb 1b |..H..T....(.....|
00000010 d2 e6 f2 24 b5 68 b4 0f 62 ae b6 51 9a 35 8f e5 |...$.h..b..Q.5..|
00000020 2c f5 4a b4 7e fc 4b f4 20 f3 2a 24 a1 99 de 88 |,.J.~.K. .*$....|
00000030 95 d6 b3 a4 9a b4 78 ed 55 c3 2a 53 ed 3e f3 17 |......x.U.*S.>..|
00000040 8e 3b 6f 6c 0a 51 4b ce 0e 32 b0 73 0b 86 38 bf |.;ol.QK..2.s..8.|
00000050 9d ff 4a ab 65 68 aa 66 cf c3 d9 0c 47 3d 95 c3 |..J.eh.f....G=..|
00000060 12 e2 29 0d 92 7b 6c 24 d7 1f 62 a9 4c 8b b3 b2 |..)..{l$..b.L...|
00000070 a7 d3 04 9d 8d 5f ca 05 ed b5 33 5b 2e d6 d4 7d |....._....3[...}|
00000080 f6 1b f9 8c 24 ba e0 88 be a1 f3 8b 05 71 08 55 |....$........q.U|
...
Nothing but random-looking noise!
When the encrypted replica file is created it is initialized with the same password the user has set on the local, original database. STRIP uses SQLCipher for encryption, which provides strong key derivation:
When initialized with a passphrase SQLCipher derives the key data using PBKDF2 (e.g. OpenSSL’s
PKCS5_PBKDF2_HMAC_SHA1on some platforms.) Each database is initialized with a unique random salt in the first 16 bytes of the file. This salt is used for key derivation and it ensures that even if two databases are created using the same password, they will not have the same encryption key.
Key derviation helps protect against brute force and dictionary-based attacks, and in conjunction with a strong master password, provides the security necessary to take advantage of these cloud services. Remember that no cryptography can protect your data from a determined attacker if the master password is weak, or can be easily guessed in a brute-force or analytical attack on the database key, so choose wisely! We generally recommend users choose a reasonably long, randomized master password for STRIP, and completely avoid PIN numbers for security purposes.
STRIP’s sync system is bi-directional, meaning that changes from more than one replica or instance of STRIP can be exchanged on each sync. Thus you can sync STRIP on your Android, STRIP on your iPhone, and STRIP on your PC all against the same Dropbox or Google Drive account. One of the major advantages of syncing with these cloud services is that they operate over HTTPS, which is rarely blocked on most networks. This means as long as you have a network connection you can usually sync to make sure you’ve got the latest data on your device.
That’s really all there is to it!
Cloud-based synchronization certainly isn’t for everybody, and many people are naturally distrustful of Cloud security, but STRIP goes to great lengths to protect your data and make sure that unencrypted contents are never stored in third-party services.
We’ve tried to make the Sync feature in STRIP for the Dropbox and Google Drive cloud services as straight-forward and secure as possible. In the future, we’re planning to make synchronization even easier through a background service that doesn’t need to be initiated by the user. This is a problem we’re working on now, though we’re being careful to balance security and ease-of-use, since the two are sometimes at odds!2
1 Usually we use the provided API from Google or Dropbox with the exception of STRIP for Windows which simply places the replica strip.db file in your local Dropbox folder, with the expectation that the Dropbox sync client is running on that computer and will handle the upload accordingly.
2 Security researcher Dan Kaminsky has a really great article on this very topic that’s quite timely.