Verifying Codebook Downloads
Introduction
Codebook is an application that runs natively on four different operating systems: Android, iOS, macOS, and Windows. Each platform has its own mechanisms for delivering software to your device securely, either through a store or some sort of direct download. Since documentation of the security of the iTunes App Store, Mac App Store, and Google Play store is pretty readily available for those vendors, this article will focus on the security of downloading the Windows and Mac versions of Codebook directly from zetetic.net. We'll also discuss protections in place to protect you from downloading malicious binaries posing as Codebook.
HTTPS
We always distribute Codebook downloads over HTTPS, and redirect all of our HTTP requests on zetetic.net to HTTPS, so it would be extremely difficult to download either the Mac or Windows version without an encrypted connection. Using HTTPS not only helps to ensure the privacy of your download, it makes it difficult (though not impossible) for an actor to intercept the communication and send some other data to you instead. At the time of this draft (currently Oct 7th, 2020) the encryption certification we use for HTTPS is a 2048-bit key certificate issued by Thawte, SHA-256 fingerprint: 87 95 DE 63 CA 68 AA FF 00 4B 0A 9B 51 4E B6 A6 78 25 3A 70 DB 19 65 93 AC 8D 54 B7 7B 3A 33 42
Verifying macOS Downloads
Codebook for macOS (the direct version, not the Mac App Store version) is distributed as a signed and notarized Disk Image that contains a signed and notarized macOS application (Codebook.app). Both are signed with Zetetic's Developer ID Certificate from Apple. macOS has a feature known as Gatekeeper that verifies the binary has been signed by Zetetic and that it hasn't been tampered with in any way (changing the binary invalidates the signature).
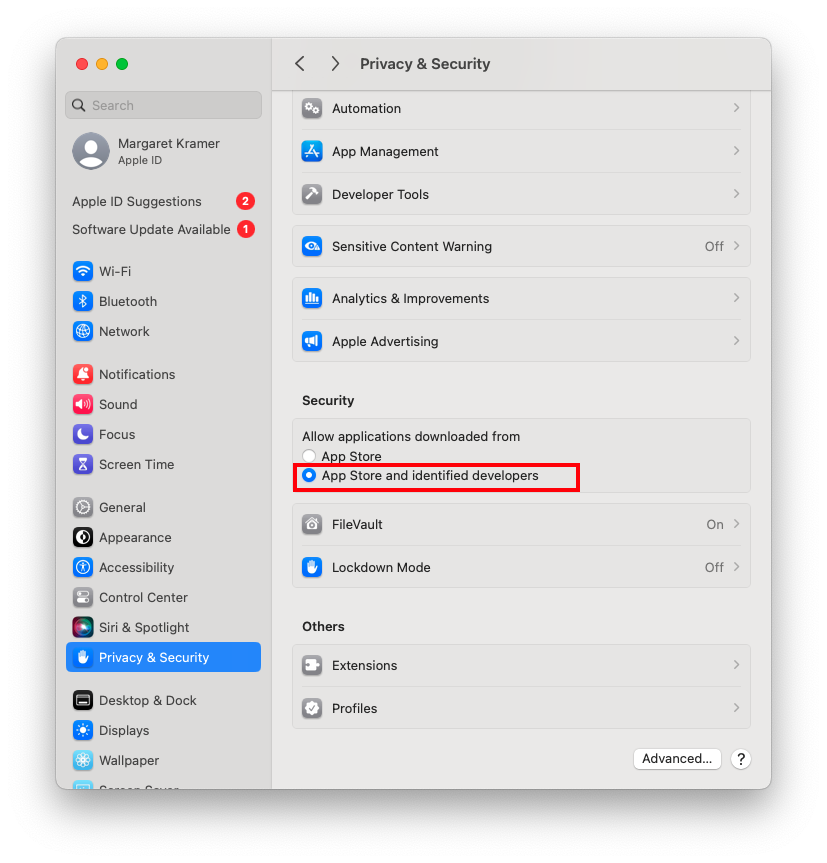
To enable (or confirm) this behavior on your Mac, go to System Settings > Privacy & Security, and ensure that "App Store and identified developers" is checked under "Allow apps downloaded from:"
You can also check via the command line to see whether or not the downloaded app is validated using the system security policy tool in Terminal:
$ spctl -a -vv --type execute /Applications/Codebook.app /Applications/Codebook.app: accepted source=Notarized Developer ID origin=Developer ID Application: Zetetic LLC (PD7G6HRMGV)
In the output in response to our command above we can see that the system security policy (Gatekeeper) has validated Zetetic's signature and the integrity of the binary. If someone were to modify the binary for malicious behavior, the code signature would be invalidated, and the check above would fail. At that point you'd no longer be able to launch the application.
Verifying Windows Downloads
Codebook for Windows is distributed as an MSI installer package. The installer and the application itself are code-signed using Microsoft Authenticode technology. Code-signing Codebook for Windows allows a user to ensure the integrity and authenticity of the application on their machine. When the installer and application are code-signed, a digital signature is embedded within the files that can then be verified by Windows later. If the application binary was tampered with, the digital signature would become invalid and the user would be notified upon execution.
Code-signing alone is not enough, as malware too can be code-signed. Windows includes a feature called SmartScreen that is used to validate the reputation of an application. While many components are taken into account when determining the reputation score, code-signing is one part in which the origin of the software publisher, identified by the digital signature are utilized.
During installation, Windows will validate the digital signature embedded within the installer. The User Account Control displayed below during an installation shows the verified publisher based on the code signature:

You can also manually check the status of the of the Authenticode signature embedded in either the application or the installer package by executing the following commands from PowerShell:
(Get-AuthenticodeSignature "C:\Program Files (x86)\Zetetic LLC\Codebook\Codebook.exe") (Get-AuthenticodeSignature "CodebookSetup.msi")
An example of running these commands can be found below:
