A customer wrote us regarding recent reports of vulnerabilities to the Keychain in iOS and OS X and whether or not these affect STRIP password manager:
Is STRIP for iOS vulnerable to this “0 days flaw” in Apple software and allows “cross-app resource access (XARA) attacks”? Is the password for the iOS STRIP app stored in the keychain of the iOS or anywhere else in the iOS system other than in the STRIP app itself?
STRIP does not store the user’s master password in the iOS or OS X Keychain (back to this in a moment).
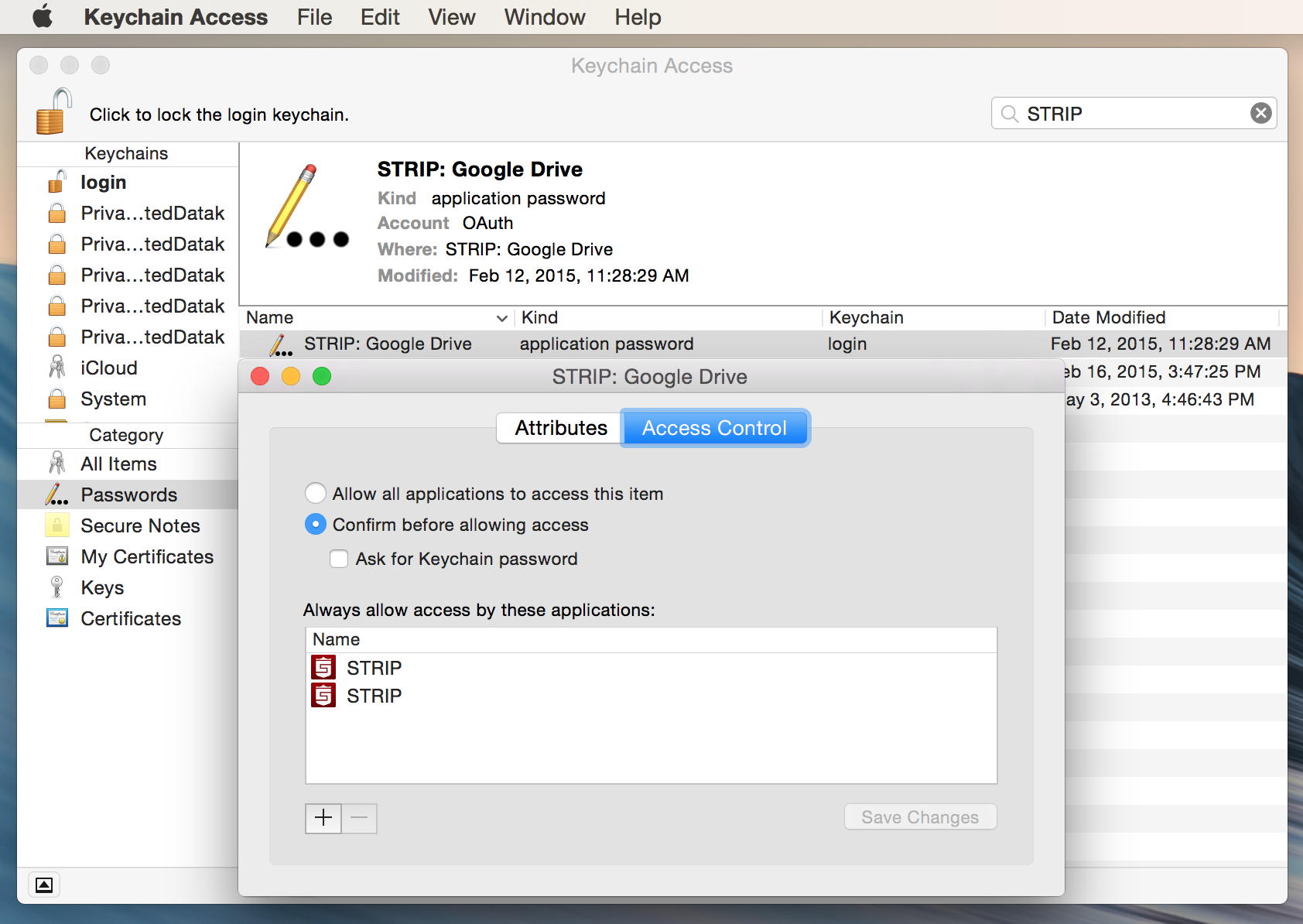
However, STRIP makes use of the Dropbox and Google-supplied frameworks for authenticating against their services for sync if you choose either of these sync modes. Both of those frameworks store the OAUTH authentication credential in the iOS and OS X Keychains (open Keychain Access on your Mac and search for “STRIP” to have a look).
Touch ID Authentication on iOS
In the soon-to-be-released version of STRIP for iPhone and for iPad we’ve added the oft-requested feature of Touch ID login. This feature is completely optional, disabled by default, and only available on devices with Touch ID. The feature works by storing your master password for STRIP encrypted in the Secure Enclave on the device, through the Keychain.
Are these Keychain items vulnerable to attack?
It depends. There’s a great article on iMore.com explaining the attacks and what’s vulnerable (emphasis theirs):
Contrary to what some reports have said, while a malicious app cannot read your existing keychain entries, it can delete existing keychain entries, and it can create new keychain entries that are readable and writeable by other, legitimate apps. This means a malicious app can effectively trick other apps into saving all new password entries to a keychain it controls, and then can read.
iOS is unaffected:
The researchers note that one of the reasons iOS is unaffected by this is that iOS doesn’t have ACLs (access control lists) for keychain entries. Keychain items on iOS may only be accessed by an app with a matching bundle ID, or group bundle ID (for shared keychain items). If a malicious app created a keychain item that it owned, it would be inaccessible by any other app, making it entirely useless as any sort of honeypot.
Using the Touch ID login feature in the next version of STRIP for iPhone and iPad should not leave you vulnerable to this exploit.
In the end you always want to avoid suspicious, maliciously crafted software; once a host operating system is compromised it becomes very difficult to keep your data secure. Watch out for phishing attacks, where email is crafted to trick you into visiting a malicious website or downloading malware posing as normal attachments. On OS X you can limit the apps allowed to run on your Mac to those signed by Apple or by Apple-identified developers (like Zetetic):
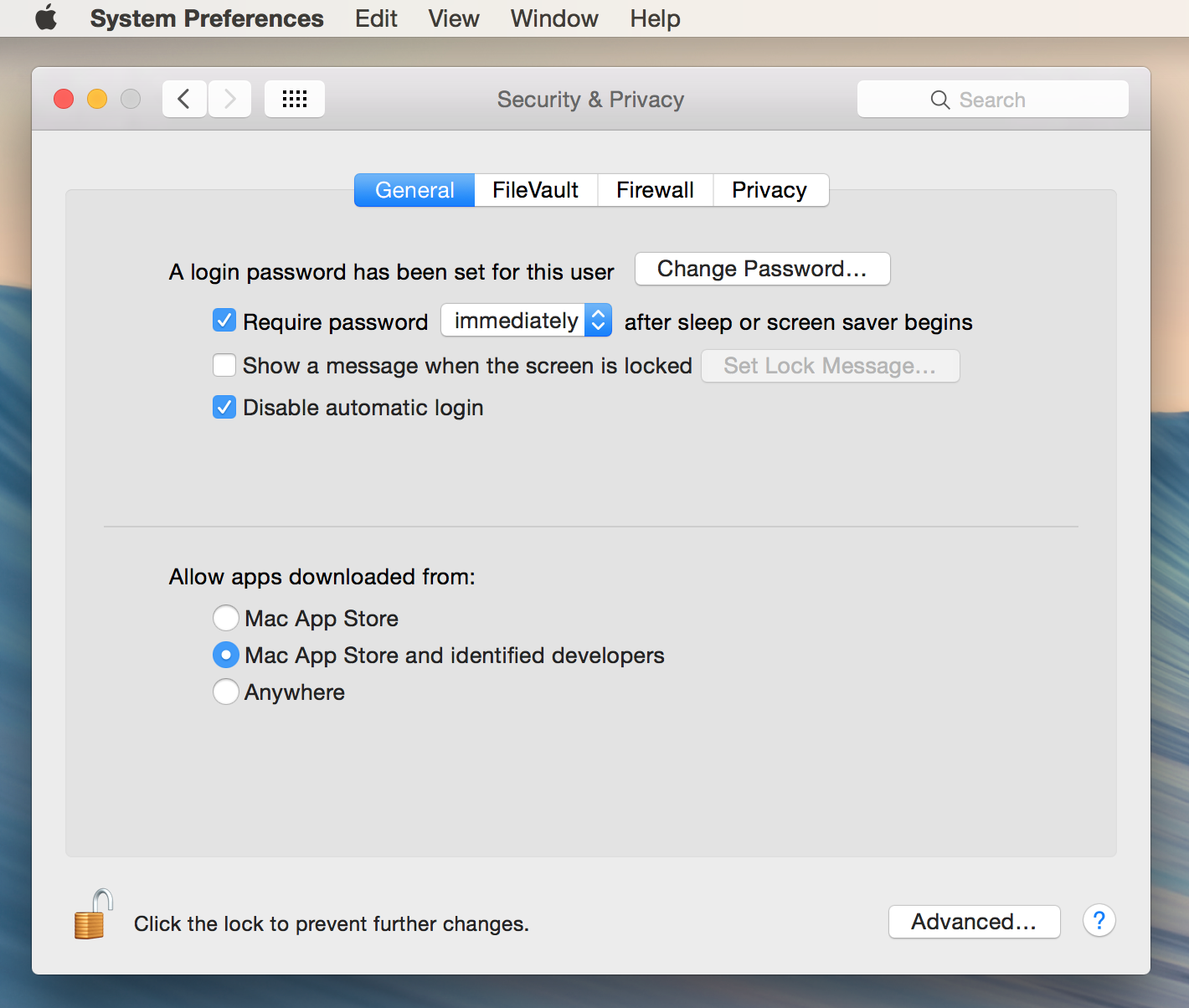
If you are concerned about malicious keychain entries you can check for them easily:
- Open Keychain Access
- Search for “STRIP”
- Select the Keychain item in the right pane and select File -> Get Info (or type command+i)
- Select Access Control
- In the list of allowed applications you should only see STRIP
What about WebSockets?
While STRIP on the Mac provides a utility function for looking up your passwords and inserting them in other applications, it does not include a browser plugin and makes no use of WebSockets, another point of vulnerability detailed in the recently announced exploits.

We are happy to announce the availability of commercial licenses to SQLCipher for Cordova. Cordova allows a developer to quickly develop mobile applications using JavaScript and now secure database storage via SQLCipher is available as a commercially supported platform. SQLCipher for Cordova provides support for integrating a SQLCipher database within a Cordova project running on iOS, Android, and Windows Phone. All interactions will the database are perform through a simple JavaScript API. Now available for purchase or as a trial.
We are happy to announce the availability of SQLCipher 3.3.0. This release is based on the upstream SQLite 3.8.8.3 release which included many beneficial updates including a general performance increase of over 20% for the same number of CPU cycles from the previous release. Specifics for the SQLite 3.8.8.3 release are covered here.
Directly within SQLCipher we have included a few additional items as well. First, we introduced a new PRAGMA, cipher_default_page_size, a mechanism which facilitates setting a non-default page size value to be used when attaching databases. Next we have added API hooks to support FIPS integration within the OpenSSL crypto provider. SQLCipher for Android has also been updated with community edition binaries available here. Binaries that ship with support for OpenSSL have been upgraded to the latest 1.0.2a release. Commercial binary updates to be available soon.
At the Daring Fireball blog John Gruber notes that he and his co-conspirators at Q Branch have increased the price of their excellent note-taking app Vesper:1
Put another way, we’re going to charge something sane or die trying. We tried following the iOS App Store trend by pricing Vesper at just $2.99 for months. It didn’t work. Prices like that are not sane, and not sustainable, at least for well-crafted productivity apps. So Q Branch is drawing a line in the sand, and we hope other iOS developers will follow.
We’re doing the same for our password manager app, STRIP. For a long time we’ve charged pretty low prices for both STRIP for iPhone (and for iPad), and STRIP for Mac: $4.99 and $9.99, respectively. The Android and Windows versions, same deal. Prices this low are not sustainable when we’re doing steady, iterative design and development while maintaining the apps and adapting them to major new hardware and operating system changes.
With the release of the 2.5 series of STRIP for Windows and OS X we’ve increased our prices. STRIP is now $9.99 on Android and iOS, $19.99 on OS X and Windows. The desktop releases are now available as 14-day free trials, which should help people get a feel for the software before deciding whether to make a purchase.
If you’ve purchased STRIP, thank you for supporting our work, it means so much to us!
1. I’ve always wanted Codebook to be more like Vesper, having based it on John’s writing on “The Untitled Note Problem,” and I love the design decisions that they’ve made.
I recently had the opportunity to bend the ear of Brent Simmons, one of the Q branch team making Vesper, during the CocoaLove2 conference in Philadelphia last October. I couldn’t help pitching SQLCipher as a datastore for Vesper. He listened thoughtfully and it was great having the chance to talk. Following the writing of these folks over the last few years has been really educational for me as a software developer and designer.
2. Yes, a footnote for a footnote! CocoaLove was fantastic. I highly recommend it. Check out the talks by William Van Hecke and Laura Savino to see what I mean.

STRIP for OS X 2.5.0 was released about 12 days ago, just wanted to make a note here for any who hadn’t seen the post in our discussion forum. For Mac App Store customers, the update should be available soon, the app is currently under review. This may be the nicest release of this version yet, with a lot of bug fixes, an improved login experience, window handling, and auto-suggest for frequently used values.



